Kovter – Malware of the Month, October 2019
The war against malware is heating up. Anti-virus software solutions are intelligently evolving to stay a step ahead of crafty, rapidly proliferating malware types. However, some ingenious forms of malware have stood the test of time and bypassed detection. They remain unseen to the most cutting-edge anti-virus scans. And they stay devious thanks to inventive updates from their cult-like following of hackers. Invisible malware and Emotet are prime examples of such irrepressible malware. Another sturdy one is the subject of this Malware of the Month spotlight – the Kovter malware.
What is Kovter Malware?
Kovter is an invisible fileless type of malware that targets Windows systems. It evades being detected by heavily relying on the computer’s registry itself to store its configuration data, thus avoiding traditional endpoint file scanning. Kovter has also stayed resilient by evolving – from a trojan-based ransomware that scared victims into believing it was the police charging fines for “illegal” internet activity to a click fraud malware and then to a fileless one. These features have made Kovter a mainstay in the Center for Internet Security’s ranking of the most prolific malware over the past few years.
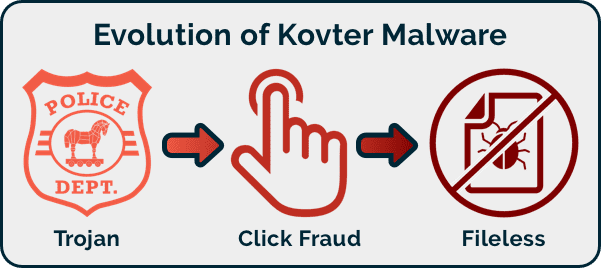
How does the current Kovter avatar work?
Kovter’s main attack vectors are malspam sent as attachments via phishing emails. Once clicked, the malware installs itself in the registry. It then uses registry keys and PowerShell executables to gain persistence, while unleashing itself in a fileless, and hence undetectable manner.
Pointers to protect your organization from Kovter
- Look out for red flags: Fileless malware is tough to detect, but as Kovter traverses via PowerShell, checking for unusual PowerShell alerts and monitoring the Task Manager for processes such as mshta.exe or powershell.exe may help.
- Educate about Phishing: With phishing being the main vector, educate colleagues across the organization about good security hygiene such as checking the sender’s email ID, not auto-downloading attachments and alerting support about emails with a threat or bait.
- Don’t let your guard down: Ensure that your firewalls, anti-spam filters, anti-virus tools, etc are robust and auto-updated. Employ measures to sandbox emails to limit the damage, if possible. Likewise, check that you have network security controls in place, particularly around shared document repositories like One Drive or Team Sites, as just one weak link can cause malware to spread throughout the organization
In the worst-case scenario of a malware attack ensure that you have an accurate, up-to-date copy of your valuable data to ensure smooth business continuity and seamless disaster recovery. All possible only with a reliable backup and restore solution.
Recover from data loss in minutes.