Simply Smarter SaaS Backup for Microsoft, Google and Salesforce.
Spanning proactively defends mission-critical data with automated backup
that is secure, affordable and insanely easy to use.
Spanning proactively defends mission-critical data with automated backup
that is secure, affordable and insanely easy to use.






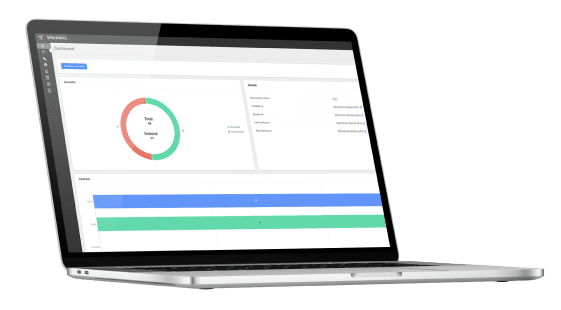
Complete protection against accidental (or malicious) deletions
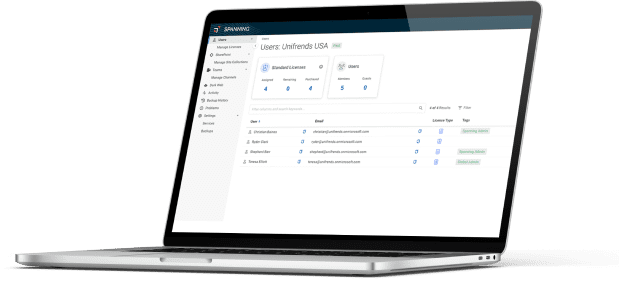


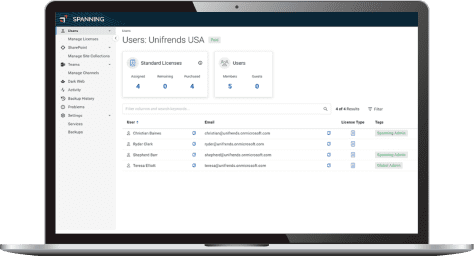

Backup for your critical Gmail, Drive, Shared Drives, Calendar, and Contact data.


Backup for your critical Office, Mail, Teams, Calendar, OneDrive and SharePoint data.


Backup for your critical Salesforce records, attachments, metadata, customizations and more.


Provide your customers with enterprise-class SaaS
backup
and recovery, with purpose-built management
functionality for
Managed Service Providers.


Ensure you can recover quickly from data loss or corruption
and keep your business moving
– no matter what.
2.4M users protected