Cloud and Data Security
CybersecurityData Protection Solutions: Safeguard Your Data From Cyberattacks & Other Threats
“Data really powers everything that we do.” — Jeff Weiner, executive chairman of LinkedIn It is often said that data is the new oil, which means data is the most valuable resource in the world currently. Irrespective of what data scientists and experts might say, in today’s data-driven business environment, information is one of […]
By
Shyam Oza
8 minute read
“Data really powers everything that we do.” — Jeff Weiner, executive chairman of LinkedIn
It is often said that data is the new oil, which means data is the most valuable resource in the world currently. Irrespective of what data scientists and experts might say, in today’s data-driven business environment, information is one of the most valuable assets an organization possesses. Sadly, many businesses don’t have adequate measures in place to protect their mission-critical data from theft, loss and corruption.
Cyberattacks continue to be the biggest threat to businesses and their data; however, that’s not the only concern. Data loss is inevitable and can occur due to several other reasons, such as human mistakes, illegitimate deletion, programmatic errors, malicious insiders and natural disasters. Verizon’s 2022 Data Breach Investigations Report indicates more than 80% breaches involved human error. A data loss incident or a cyberattack on your business can cause irreparable damage to your company’s reputation. Having a robust data protection plan is key to the survival and success of your business in this threat-laden business landscape.
The good news is that there are several modern data protection solutions available today that can protect your business from the devastating damage caused by data breaches and cyberattacks. Read on to learn more about them.
What is a data protection solution?
Before we explain what is a data protection solution, it is important to understand what data protection means. In simplest terms, data protection is safeguarding your company’s important information against unauthorized access, loss or corruption.
A data protection solution can be broadly defined as any tool, technology or technique that helps keep your valuable information safe. This may include firewall, password protection, security training, username and password authentication, data backup, business continuity and disaster recovery (BCDR) solutions and so on. These are separate layers of defense that help protect your business and data in their own unique ways. Your company may use one or more solutions depending on your needs and budget.
What is the purpose of a data protection solution?
A data protection solution, for example, a data backup and recovery solution, ensures the safety of your organization’s sensitive data by storing a copy of your data on a separate or third-party server. In most cases, these backups occur autonomously and frequently, resulting in maximum data protection. This ensures your valuable data is securely backed up and readily available for recovery in the event the data is compromised, lost or stolen. Data protection solutions, such as a backup and recovery tool, help minimize downtime and business disruption, enabling you to quickly get back up and running in no time.
Data protection vs. data security solutions
Data protection and data security solutions are closely connected, with the terms often used interchangeably. Data protection solutions are part of a larger strategy that includes data security. Data protection solutions ensure data availability and accessibility, enabling authorized users to access data in a timely and secure manner to perform day-to-day activities. This is also applicable during data recovery, where they can quickly find and restore lost and/or corrupted data.
On the other hand, data security solutions keep data secure from unauthorized access, manipulation and disclosure. Data security solutions may include administrative controls (privacy policies), physical security, disk encryption, access control and data masking, to protect critical assets against malicious activities as well as insider threats and human negligence. Some of the data protection techniques are data backup and recovery, archiving and replication, to name a few.
Why is it important to have a data protection solution?
The volume of data in the world is expected to increase to more than 180 zettabytes at a compound annual growth rate (CAGR) of 28% by 2025. This includes data created, captured, copied and consumed. While on one side, the volume of data is increasing exponentially, on the other, the number and cost of data breaches also continue to reach new heights. Verizon’s 2022 Data Breach Investigations Report revealed 5,212 confirmed ransomware-related data breaches, indicating a 13% increase, which is more than the last five years combined. IBM’s 2022 Cost of a Data Breach Report indicates the average cost of a data breach increased 2.6% to reach $4.35 million in 2022. These numbers indicate how important data and its protection has become for businesses today.
Your company holds critical information related to your employees, clients, business partners, suppliers or stakeholders. The data may include Personally Identifiable Information (PII) like names, addresses, birth dates, telephone numbers, social security numbers, email addresses, banking details, medical records or intellectual assets. Protecting this confidential data is not only crucial for the survival and success of your business but also a mandate from regulatory authorities.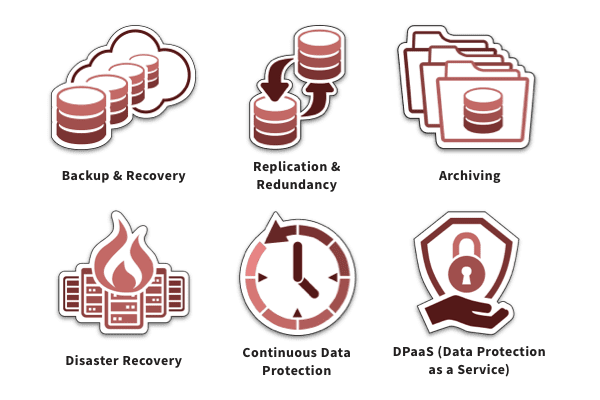
Common data protection solutions
Massive data volumes coupled with rising cyberattacks make data protection a challenge for both large and small businesses. However, with the right knowledge and tools, your organization’s data protection efforts can be significantly improved. Here are some common data protection solutions and techniques that modern businesses use to safeguard important information from unwanted access, theft and exposure.
Data backup and recovery
A data backup and recovery solution is an absolute necessity to keep your business going even in case of a data loss or a cybersecurity incident. Data can be lost, damaged or stolen due to human mistakes, malicious attacks or natural disasters, which can disrupt business operations. By having copy/copies of your critical data securely stored in a secondary location, you can quickly recover from any catastrophic event with minimal or no downtime.
Data replication and redundancy
Data replication is the process of making multiple copies of the same data and storing them in different locations, such as two on-premises software instances or appliances, between appliances placed in separate locations or two completely geo-physically separated appliances via cloud-based services. This helps businesses improve data availability and accessibility.
Data redundancy is the process of keeping mission-critical data across multiple data centers that reside in different geographic locations. This ensures your business continues to function as normal even if something happens to the data on the primary site or in the event the primary site fails.
Data archiving
Data archiving is the process of keeping data and files, not used/needed on a daily basis, for long-term storage for future purposes. Data archiving is useful for eDiscovery and legal hold in case of litigation and meeting compliance requirements; however, it isn’t useful for business continuity.
Data protection is VERY different from archival. Many companies confuse the two since they both create and store a copy of data. Some are of the opinion they don’t need an archive since they have a backup, while others say they don’t need a backup since they have an archive. Both factions are wrong. Backup and archiving have their own specific purposes and must work in tandem to improve your company’s overall data protection strategy.
Disaster recovery
Disaster recovery comprises of processes and techniques that help businesses recover from and resume normal operations in the aftermath of a disaster. Disaster recovery is part of a business continuity plan that focuses on restoration of mission-critical IT applications and data in case of cyberattacks, natural disasters, hardware/software failures or outage.
Continuous data protection
TechTarget defines continuous data protection (CDP) as “a backup and recovery storage system in which all the data in an enterprise is backed up whenever any change is made.” CDP is also known as continuous backup or real-time backup. One of the main advantages of CDP is that it keeps a record of every change being made to data. It safeguards data against viruses, malware and accidental deletion by enabling point-in-time restoration of lost/infected files.
Data Protection-as-a-Service (DPaaS)
Techopedia defines Data Protection-as-a-Service as “a cloud-based or web-delivered service for protecting data assets.” This model is ideal for businesses of all sizes and is especially useful for companies that operate with limited budgets or skilled resources. Most DPaaS vendors offer three major services:
Backup-as-a-Service (BaaS): This service allows businesses to safely back up data to the cloud and enables quick recovery in case of a breach or data loss.
Disaster-Recovery-as-a-Service (DRaaS): With this service, businesses can move critical applications, data or servers to the cloud. DRaaS enables organizations to continue business operations even during and after a disaster by providing quick restoration and access to critical systems and data.
Storage-as-a-Service (STaaS): This is a cost-effective backup service that uses on-premises storage systems instead of the cloud to store copies of data. This is a cheaper alternative to private storage infrastructure and is ideal for small businesses and startups.
Data protection with Spanning Backup
Most businesses understand the basics of data protection but miss out on the new trends and changes, or they don’t understand the value of having an integrated solution or layered defense. For instance, many businesses today use three or more data protection solutions, which not only increases IT burden and costs but also hampers productivity.
Data solutions that work or integrate with data security solutions offer a superior experience compared to standalone tools. For example, a backup and recovery solution can help recover your lost data. However, if your data protection solution is integrated with a data security solution like Graphus, for instance, you will be warned even before data loss occurs since your credentials will be monitored on the dark web, or even better if the credentials are never compromised in the first place because users are protected. Sounds interesting?
Spanning 360 comes integrated with Graphus, the world’s first automated phishing defense platform, to deliver enterprise-class, end-to-end data protection solution for Microsoft 365 and Google Workspace. Its advanced capabilities help prevent, anticipate and mitigate account compromise and data loss caused by phishing, ransomware attacks, human error, malicious behavior, and configuration and sync errors.
Work with confidence in the cloud.
Learn more about Spanning 360