Cloud and Data SecurityDenial-of-Service (DoS) Attacks — Web-based Application Security, Part 7
A Denial-of-Service (DoS) attack is when legitimate users are unable to access a network. Learn how they work and how to protect against them.
By
Shyam Oza
5 minute read
Identifying and resolving vulnerabilities in your web-based application security is vital to the smooth running of your website. In this series on security, we discuss Denial-of-Service (DoS) attacks to shed light on a vulnerability that, when exploited, results in the complete shutdown and inaccessibility of a network to its actual users.## What Is Denial-of-Service Attack?
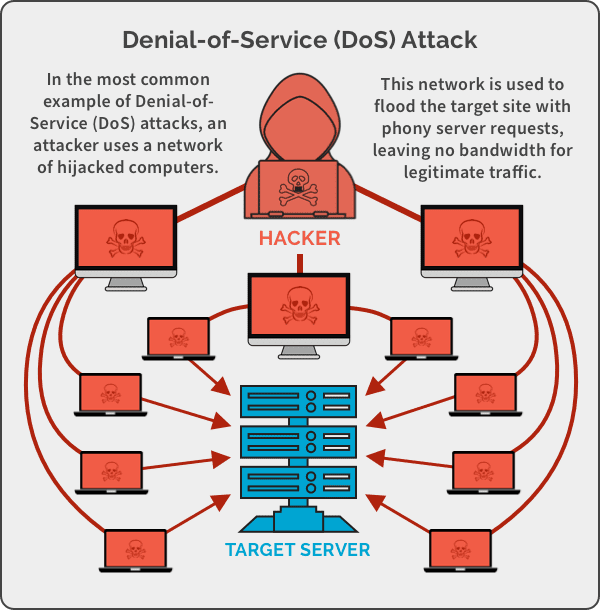
A denial-of-service (DoS) attack is when legitimate users are unable to access the network they use as well as websites, emails and other services that rely on the network. The attack is launched using a single computer – typically flooding the network with traffic – until the network cannot respond or crashes.
The ease of deploying DoS attacks makes it a hacker’s dream while the time and money that it costs to recover from these attacks make it an organizational nightmare.
However, since hackers prefer effectiveness over convenience, they switched to a different but more advanced form of DoS attacks, known as Distributed Denial of Service (DDoS) attacks, to counter more resilient networks.
The Difference Between DoS and DDoS
DoS and DDoS are two different names for the same attack. DDoS has been incredibly effective as a threat and is considered one of the top cybersecurity trends of 2020.
| DoS | Points of Difference | DDoS |
|---|
| A single computer and IP address is used to launch an attack. | Source | The source of the attack comes from multiple locations that include compromised computers, webcams and IoT devices. |
| DoS attacks are initiated using scripts or tools like Low Orbit Ion Cannon. | Tools | DDoS attacks are initiated with botnets. |
| DoS attacks are slower to execute. | Delivery Speed | DDoS attacks are faster to execute. |
| Easier to block. | Blocking Attack | More difficult to block due to the volume of machines used to execute the attack. |
| Easier to trace since only single device is in play. | Traceability | Tracing the true party is challenging since they can hide behind various compromised systems. |
| Buffer Overflow, Ping of Death, Teardrop | Attack Types | Volumetric, Fragmentation, Application Layer |
How Does a DoS Attack Work?
DoS attacks are not like your typical malware attacks. They don’t require special programs to run. Instead, they seek to exploit the inherent vulnerability in the target network.
Let’s say you’re looking to buy your favorite pair of sneakers from your favorite ecommerce website. Typically, your device sends a small packet of information asking the server for authentication. Once the server authenticates and your network acknowledges the approval, you can access the website.
However, in a DoS attack, the process is rigged. Bad actors send several packets of information asking the server for authentication. The problem is the return address is faulty, thereby making it impossible for servers to send the authentication approval. The server must wait a long time before closing the interaction. When it does close, a new batch of forged requests are sent and the server will have to restart the entire process again.
As a result, your favorite ecommerce site starts showing these symptoms:
- Inability of users (you) to access the website
- Slow network performance
- Failing to load site pages
- Loss of connectivity across devices on the same network
 ## The Different Types of DoS Attacks
## The Different Types of DoS Attacks
Here are a few of the different types of DoS attacks:
Buffer Overflow
Buffer Overflow is a common type of DoS attack. It relies on sending an amount of traffic to a network resource that exceeds the default processing capacity of the system. For instance, back in the day, a 256-character file name as an attachment would surely crash Microsoft Outlook.
Ping of Death
Attackers send spoofed packets that ping every computer on the targeted network. The target responds and becomes flooded with responses from the malicious packet. It is also known as Internet Control Message Protocol (ICMP) Flood and Smurf Attack.
SYN Flood
A SYN Flood attack exploits the Transmission Control Protocol (TCP) handshake – a method used for the TCP network to create a connection with a local host/client/server. Unfortunately, the handshake is left incomplete, leaving the connected host in an occupied status and unavailable to take further requests. Attackers will double down on the requests, saturating all open ports and preventing anyone from connecting to the network.
Teardrop
In a teardrop attack, IP data packet fragments are sent to the target network. The network then reassembles the fragments into the original packet. The process of reassembling these fragments exhausts the system and it ends up crashing. It crashes because the fragments are designed to confuse the system so it can never be put back together.
The Real Motivation Behind DoS Attacks
A deer hunter uses a decoy to pull the deer in close. With the deer focused on the decoy, hunters get better opportunities for a good shot. Similarly, a DoS attack is the decoy, the hacker is the hunter, and guess who the deer is?
That’s right. You!
Businesses are often fearful that DoS attacks will impact sales, but they should be just as concerned, if not more concerned, about data theft. Peel through the surface and you will find that DoS and DDoS attacks are used to draw attention away in order for hackers to launch secondary attacks elsewhere on your network.
A staggering 92 percent of companies that have experienced just one DDoS attack also reported some form of data theft.
Protect Your Business Against DoS Attacks
There are two approaches you can take to protect your business against DoS attacks:
Preemptive Measure
Identify DoS attacks before they cause harm by using network monitoring. Also, test run DoS attacks to see how you will fare against an actual attack so you can refine your overall strategy.
Post-Attack Response
Create a Disaster Recovery Plan to ensure proper communication, mitigation and recovery of data. A good plan can be the difference between an inconvenient attack or a devastating one.
Spanning protects your organization’s critical data from loss caused by a DoS attack and other cyberthreats. It allows administrators to quickly find and restore Microsoft 365, Google Workspace and Salesforce data to its original state in just a few clicks. This ensures business continuity even during an ongoing DoS/DDoS attack.
Want to learn more about Spanning Backup?
Let’s Talk