Cloud and Data Security
Microsoft 365Dridex — Malware of the Month, December 2019
Dridex — a malware specifically designed to attack financial services organizations and banks — is Spanning’s Malware of the Month for December 2019. Learn how it has evolved and resulted in the theft of hundreds of millions of dollars from institutions in the form of fraudulent transactions.
By
Shyam Oza
3 minute read
The malware types that cause the most damage are the ones that remain resilient due to an evolving codebase combined with features that make them notoriously undetectable. Every month we profile one such malware with pointers to protect your organization from them. Past notables have included Emotet, Trickbot, Kovter, and most recently, Zeus. A similarly potent malware is Dridex — malware specifically designed to attack financial services organizations and banks. This piece of malicious code along with its cousins “Bugat” and “Cridex” has resulted in the theft of hundreds of millions of dollars from institutions in the form of fraudulent transactions.## What is Dridex?
Dridex is a banking Trojan – a type of malware that craftily conceals its malicious intent causing users to fall prey to it. It was first detected in 2011 and has been a lucrative enterprise for its suspected creators. Two significant attacks were one in 2015 that caused $40 million in damages and a recent $100 million heist that has the FBI in hot pursuit.
How does Dridex work?
Dridex’s primary vector is via phishing and mail spam. The latest variant of Dridex, and its most powerful, disguises itself using file signatures that are undetectable to anti-virus software. Furthermore, the signed 64-bit dynamic link libraries (DLLs) used by Dridex are loaded via legitimate MS Windows executables.
Once in, Dridex targets financial information. Its range of “capabilities” span capturing banking credentials, triggering unauthorized transfers from the victims’ bank accounts, opening fraudulent accounts and using the compromised victim’s accounts as money mules for other scams.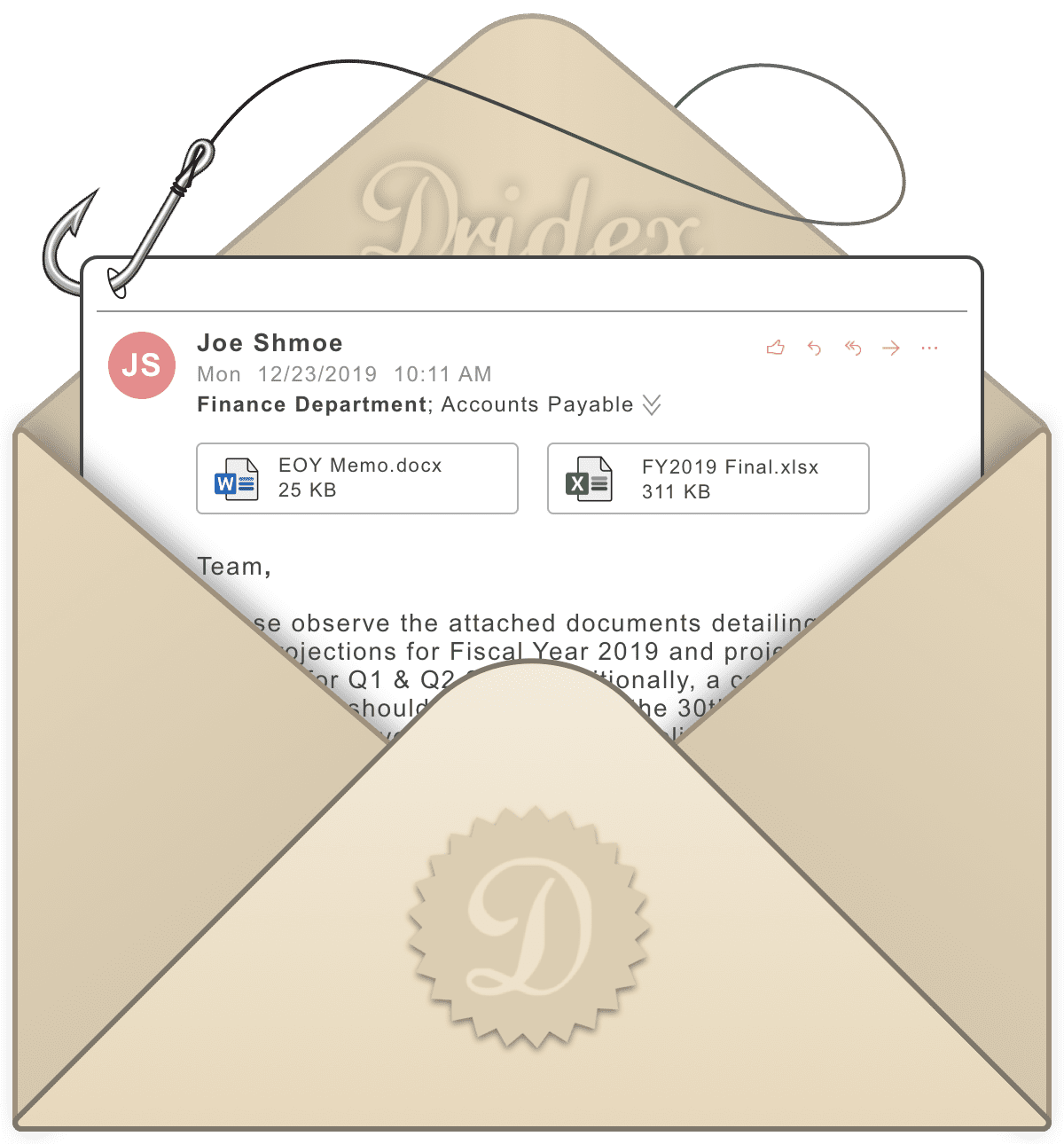 ## Tips to Protect Your Organization from Dridex Malware
## Tips to Protect Your Organization from Dridex Malware
- Dridex Alert: The Department of Homeland Security has issued a Dridex alert with detailed best-practices to protect your organization. Read through them particularly if you’re a financial services or banking organization – Dridex’s favorite target.
- Inform, Educate, Champion: The main entry point for Dridex is the mistaken click of a malicious link in an email or message. Preventing that one wrong click is your best defense in protecting your organization. Clever social engineering and personalized phishing emails can deceive even the smartest employee. Which is why training is so critical. Keep employees updated about the latest scams and the red flags they should watch out for in emails and social messages. Prevent phishing scams from taking effect with regular organization-wide cybersecurity training. For larger organizations, cultivate department-wise cybersecurity champions who alert IT Admins of suspicious emails, conduct security hygiene lunch-and-learns, and ensure that newer employees are trained in the basics of security hygiene. Keep the cybersecurity training engaging and relevant using newsletters, quizzes, videos, and posters.
- Use Anti-Phishing Tools and Policies: Microsoft 365 includes built-in features that protect your users from phishing attacks. Take advantage of the threat management tools in Microsoft 365 to set up anti-phishing policies and increase your protection status. You can even create custom policies for specific users, groups, or domains.
- Don’t Forget: Basic security hygiene – auto-update your anti-virus solutions, scan downloads, disallow macro execution, update your firewalls, network monitoring tools, and intrusion monitoring tools.
When struck with a malware attack, getting your business back on its feet with minimal damage is crucial in reducing the impact of the attack. Prepare for malware with robust disaster recovery and business continuity plans. Central to them is dependably and accurately backing up your data so you can quickly recover it and ensure business as usual. The Treasury and the Cybersecurity and Infrastructure Security Agency (CISA) also advises organizations to “conduct regular backup of data” as a top malware mitigation recommendation.
Spanning Backup for Microsoft 365 securely and comprehensively backs up your data with the provision to easily recover it from any point-in-time or at a granular level with a few clicks. Mitigate the risk of Dridex with secure backup and recovery.
Learn How Spanning Protects Microsoft 365