Cloud and Data SecurityIdentity Theft on the Dark Web: Understanding the Full Impact of a Data Breach
The dark web has made identity theft a “lucrative business” which is leading to more pervasive and ingenious attacks – often targeting your customer’s credentials. Learn how to protect your data, business reputation, and customer base.
By
Shyam Oza
4 minute read
The Dark Web is as ominous as it sounds, and then some. Also called the “darknet,” it refers to content on the internet that is encrypted and whose IP addresses are intentionally hidden. This makes them inaccessible through conventional search engines. The radical anonymity on the Dark Web has made it a home for whistleblower forums and a safe space for those under oppressive regimes at one end of the spectrum, and an underground criminal marketplace for drugs and illicit activities at the other end. ## Identities: Dark Web’s Latest Hot-Selling Item
Data breaches are increasingly targeting customer records – 4.1 billion personal records were leaked due to data breaches in the first six months of 2019 alone. The impetus for that is the profitable and viable marketplace that personal records find on the dark web. The IMF puts identities, credit card details and bank details as the second-most wanted “product” on the dark web, after contraband and pharmaceutical drugs. And lucrative it is. While website login credentials vary from $12 – $120, details of a person’s entire identity can cost upwards of $3000.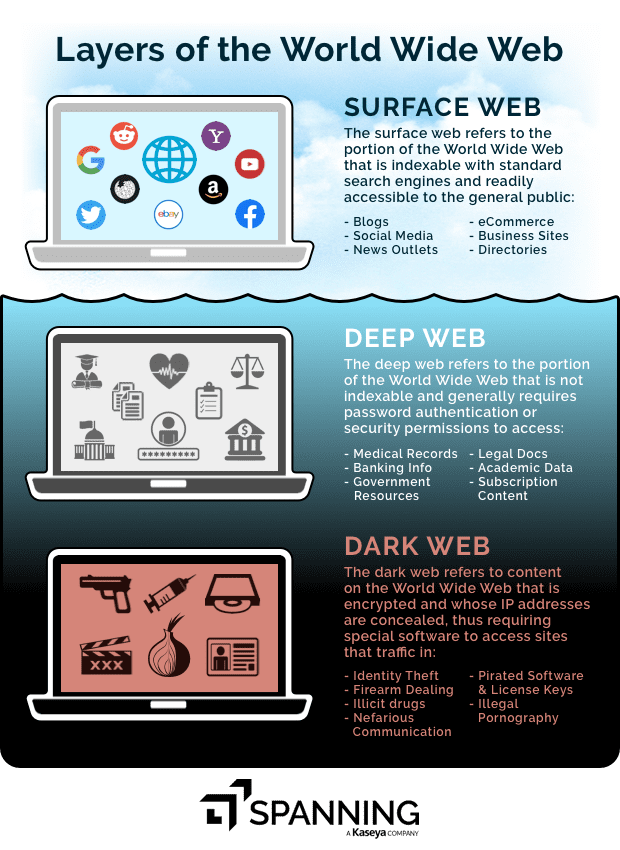 ## Breach + Theft/Malicious Deletion: A Double Whammy
## Breach + Theft/Malicious Deletion: A Double Whammy
The cost of a data breach for an enterprise has risen by 14% this year to $1.41 million. For an organization reeling under the massive cost of a breach, the damage of having their data sold on the dark web could be devastating in terms of brand reputation, customer loss, and further financial/legal costs.
Another scenario that is bleaker still, is one where hackers breach your organization and then proceed to simply wipe out the resources and artifacts that they are now in control of, causing irreversible harm to the business. A legendary case highlighting the same is about a successful IT services organization that had its business destroyed due to such a nightmarish assault. An attacker breached the company’s AWS control panel and demanded a ransom to give back control. When it was refused, the hacker started deleting resources. The company eventually gained control, but not before the deletions caused irreparable damage to the business. While cases such as these are not often made public, data breaches are known business slayers – more than 60% of SMBs cannot survive a data breach.
So, how do you protect your business and your customer’s data from ending up on the dark web or from being maliciously deleted? Firstly by preventing a data breach by making certain that your network, applications, processes, and employees abide by the highest cybersecurity best practices. Unfortunately, given the tenacity and ingenuity of hackers, it is best to be prepared for the worst-case scenario. If a breach were to occur, limit the damage and ensure business continuity with a reliable backup and restore solution that quickly recovers your data. Your final line of defense? Dark web monitoring. This applies to an intelligent identity protection solution that proactively monitors the dark web for an organization’s compromised or stolen employee and customer data.
Your Friendly Neighborhood Data Protection Crusader
Spanning protects your data from multiple fronts – it provides comprehensive, secure and automated SaaS backup, guarantees business continuity with rapid recovery, and offers integrated dark web monitoring for compromised or stolen credentials.
Additionally, when your data is backed with Spanning, you can rest assured that it is in the safest hands. We hold our product up to rigorous security standards – SOC 2 Type II, UE-EU Privacy Shield, and BBB EU Privacy Shield certifications, HIPAA, GDPR, and SSAE 16 compliance, robust 256-bit AES object-level encryption, intrusion detection and compartmentalized access – all to exhaustively safeguard your data.
Furthermore, Spanning leverages application-level security (OAuth 2.0) instead of service accounts for access to your SaaS systems, which adheres to multi-factor authentication requirements that are gradually being mandated by SaaS platforms.
Don’t risk the double danger of a data breach followed by your customer’s data leaking on the dark web. Get peace of mind with Spanning’s secure backup, quick recovery, and dark web monitoring.
Download the Most Secure SaaS Backup