Microsoft 365
RansomwareWhat You Need to Know about Ransomware Attacks and Microsoft 365
Over the past few years, there has been a stunning increase in the number and sophistication of ransomware attacks. Microsoft products and services have been targeted by cybercriminals for decades — now that Microsoft 365 is the company’s fastest-growing solution, it’s a primary target. Given the great risks for losses at the hands of cybercriminals, every member of your organization — from your COO to each individual employee — must take proactive measures to protect the organization’s data.
By
Lori Witzel
5 minute read
Over the past few years, there has been a stunning increase in the number and sophistication of ransomware attacks. As Deputy Attorney General Rod Rosenstein has stated:“…the monetary costs of global annual cybercrime will double from $3 trillion in 2015 to $6 trillion in 2021. … Cyber criminals know that a company’s lifeblood is contained in its networks and the information flowing through those systems. The last few years have witnessed a significant increase in criminals using ransomware. … Today, the attacks are concerted efforts by sophisticated individuals, criminal enterprises, or nation-states that can target a range of home users, businesses, networks, or critical infrastructure with laser-like precision to cause widespread damage.”
U.S. Department of Justice research shows that ransomware attacks quadrupled from 1,000 attacks per day in 2015 to more than 4,000 attacks daily in 2017.
Microsoft products and services have been targeted by cybercriminals for decades — now that Microsoft 365 is the company’s fastest-growing solution, it’s a primary target. Although Microsoft has recently released improvements to ransomware detection and recovery, this is still an arms race — and the cybercriminals are winning. As shown in the ransomware attack on CDOT, cybercriminals are “well-versed in evading antivirus, and may infect victims multiple times.” See additional articles below:
Ransomware attacks are devastatingly costly, with damage costs forecast to hit $11.5B by 2019. These costs include but are not limited to:
- Damage and/or data loss
- Downtime and lost productivity
- Ransom (cryptocurrency) if an organization decides to pay the cybercriminal
- Forensic investigation
- Restoration and deletion of hostage data and systems
- Damage to brand and reputation
Given the great risks for losses at the hands of cybercriminals, every member of your organization — from your COO to each individual employee —must take proactive measures to protect the organization’s data.
The Anatomy of a Ransomware Attack
At the highest level, there are three main elements common to most ransomware attacks:
- Find a way in
- Land and expand
- Encrypt and ransom
Find a way in: As shown by the recent and devastating SamSam ransomware attacks, cybercriminals don’t rely solely on social engineering as an attack tactic. Any vulnerability that can be exploited–such as systems with open ports, open RDP connections, vulnerable services exposed–will be exploited. That doesn’t mean organizations should become complacent about end user security training. As reported in CIO magazine, “Of the 80 billion messages sent to Microsoft 365 inboxes in a month… more than 20 million contain malware or phishing messages.”
Land and expand: Once your organization’s systems have been breached, ransomware can effectively shut your organization down. Ransomware can be programmed to search for critical files locally, on your networks, and in the cloud. It can contact command and control services, and finally, it can utilize access to spread to other machines. With cloud-based applications such as Microsoft 365 email, or collaboration tools such as SharePoint Online and OneDrive for Business, ransomware can proliferate at compute speed across multiple users, systems, and shared files. As a result, cybercriminals can gain full access to your organization’s data and email, and potentially destroy or harvest data.
Encrypt and ransom: Finally, ransomware, unlike other types of malware, will encrypt your files or lock down your system. Infected end user devices will receive a message that their data is being held ransom. Cybercriminals typically demand payment in cryptocurrency to unlock or release victims’ systems and data. Some cybercriminals, such as those behind the SamSam attacks, use a payment strategy designed to make it seem reasonable to pay the ransom in exchange for access, and have generally chosen to “honor” their criminal bargain with their victims. However, there is never a guarantee that a cybercriminal has not damaged your data or will return control to your organization. In many cases, your data is destroyed and inaccessible even after ransom has been paid.
Data Protection and Microsoft 365
It’s clear that ransomware risk reduction is imperative. For Microsoft 365 and other cloud apps, Spanning recommends a layered approach. The NIST Cybersecurity Framework is a great place to start if you don’t already have a plan in place. The three pillars highlighted below are most crucial and require evaluation when moving your critical business data to a SaaS application. End user training is also critical, as end users can become a “malware gateway” into your organization.
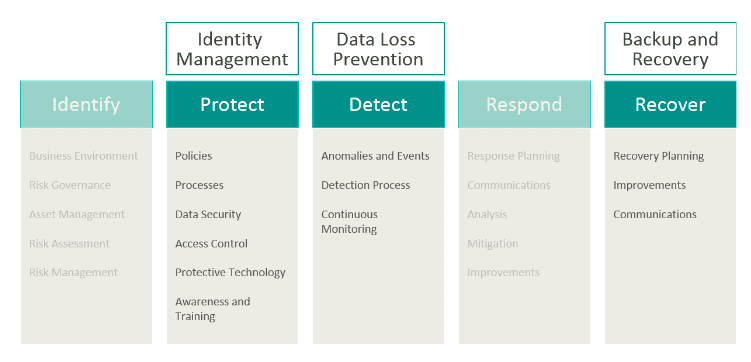
Backup and Restore Solutions
It’s vital to have tested processes in place to protect critical business data before an attack happens. Implementing a trusted backup and recovery solution is a proactive means of protecting your data and your organization. If you do suffer an attack, your organization must be able to recover quickly. Backup solutions such as Spanning Backup for Microsoft 365 can restore your critical business data to the last ‘clean’ version before the attack occurred. This restore capability also minimizes the hefty cost of employee downtime as well as eliminates the need to pay ransom.
Spanning Backup for Microsoft 365 provides enterprise-class protection for Mail, SharePoint, OneDrive for Business and Calendars. Think of it this way: many ransomware attacks are not preventable, given the ongoing increase in new variants. System vulnerabilities will be exploited. End users will always make mistakes, no matter how well-trained. And if you are attacked, there is no guarantee your data will be recoverable or returned to you.
Backup and restore solutions built for cloud apps ensure you can recover your data and bypass dealing with the ransomware attack all together.
Learn More
View “How to Recover from a Ransomware Disaster” presented by Mat Hamlin, VP of Products, and Brian Rutledge, Senior Security Engineer.
Why You Need SaaS Backup