Cloud and Data Security
CybersecurityPassword Spraying: What It Is and How to Prevent It
Password spraying is a high-volume brute force attack that takes advantage of users’ bad password practices. Learn how it works and how to prevent it.
By
Spanning Cloud Apps
7 minute read
With cybercrime continuing to grow in both frequency and intensity, no business connected to the internet is safe. According to the FBI’s Internet Crime Report 2021, the Internet Crime Complaint Center (IC3) received a record 847,376 complaints in 2021 — a 7% increase from 2020. Similarly, the Federal Trade Commission’s (FTC) Consumer Sentinel Network recorded over 5.7 million reports filed by consumers in 2021, of which 25% were for identity theft. Despite surging cybercrime rates, many businesses do not implement strong authentication technologies like two-factor authentication (2FA) or multifactor authentication (MFA).
Cyberthreats are constantly evolving and becoming even more complex, aggressive and harder to detect. Sophisticated techniques used by threat actors today are capable of bypassing even the most advanced security systems. That being said, cyberattacks of any nature or scale — from a highly advanced ransomware attack to a comparatively simpler password spraying attack — can have a devastating impact on businesses of any size. In this article, we take a closer look at password spraying, how it works and how to better protect your business and data against it.
What is password spraying?
Password spraying is a type of high-volume brute force attack. In this type of attack, the threat actor attempts to gain unauthorized access to accounts by using a list of commonly used passwords on a large number of usernames. For example, an attack will use a password (i.e., P@ssword123) or a small list of popular passwords and attempt to log in to many different accounts on the application.
A password spraying attack takes advantage of users’ bad password practices. This technique is also known as “low-and-slow,” since the attacker maintains a gap between each login attempt to avoid detection and account lockout.
Password spraying vs. brute force
A brute force attack is a trial-and-error method where the attacker attempts to compromise an account by guessing the password. As the name suggests, the attacker tries to forcefully access user account(s) by trying to match a list of passwords against a username with the hope that one of the combinations match. This continues until the attacker finds the correct match.
Brute force attacks are not feasible for today’s smarter applications where account lockout policies can be implemented. These applications can detect a possible intrusion and block the account after a few failed login attempts. Brute force attacks are time-consuming since the attacker has to space out attacks to avoid being detected or locked out.
Password spraying is arguably the improved version of brute-forcing, capable of evading intrusion detection and account lockouts effectively. Password spraying is similar to brute-forcing since both methods are trial-and-error and they attempt to guess the correct password. However, in a brute force attack, the threat actor utilizes multiple passwords to attack one account, while in a password spraying attack, the attacker targets high volumes of usernames with a few commonly used passwords.
Password spraying vs. credential stuffing
Password spraying attacks involve using a small list of passwords against a large number of user accounts. However, in credential stuffing attacks, threat actors use automated tools to match sheer volumes of usernames and passwords across multiple sites, until one of the login credentials matches. Today’s advanced credential stuffing programs are capable of evading the built-in security features in web applications. They leverage bot technology to conduct several login attempts simultaneously while disguising IP addresses, making them appear as if they were coming from different sources.
How does a password spraying attack work?
- A threat actor begins by building or acquiring a list of accounts to spray against. Most businesses follow a formal convention for email addresses (i.e., firstname.lastname@companyname.com). Once the threat actor deciphers the username pattern, it is easy to create accounts and validate the same using software.
- Once the accounts are validated, finding a list of commonly used passwords is relatively easy. The perpetrator may determine the password by searching publications for the most common passwords each year, or through a simple search on Google or Bing. The attacker may also scan through social profiles for details such as date of birth, family member names, favorite sports team, address and so on. For example, a combination including “Patriots,” is a popular choice in the Massachusetts area. After carefully selecting a password, it is tested against all the usernames in the list. If the first attack is unsuccessful, the threat actor will wait for a certain period to avoid triggering a lockout, and then try the next password.
- This process continues until one of the username and password combinations works and allows the threat actor illegitimate access. The threat actor now has access to all the accounts and services the user has access to such as cloud resources on SharePoint or OneDrive. The hacker may use the exploited account to gather intelligence on the target network or get privileged access to get deeper into systems.
What is an example of a password spraying attack?
Here is an example of how a password spraying attack is carried out: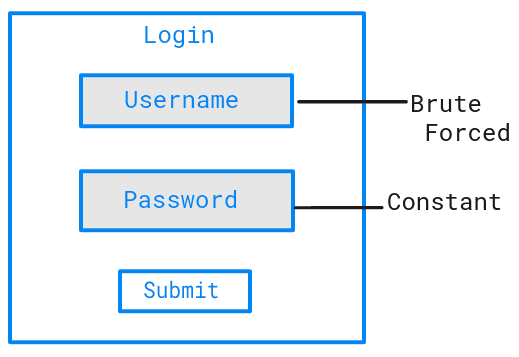
What do password spraying attacks target?
It’s common for threat actors to target management services over commonly used ports when password spraying. Many of the common services include:
- SSH (22/TCP)
- Telnet (23/TCP)
- FTP (21/TCP)
- NetBIOS/SMB/Samba (139/TCP and 445/TCP)
- LDAP (389/TCP)
- RDP/Terminal Services (3389/TCP)
- HTTP/HTTP Management Services (80/TCP and 443/TCP)
- VCN (5900/TCP)
- MSSQL (1433/TCP)
- Oracle (1521/TCP)
- MySQL (3306/TCP)
- Kerberos (88/TCP)
Beyond management services, password spraying attacks are commonly found to target applications using single sign-on (SSO) and federated authentication, or where IT administrators create a default password for setting up new users as well as externally facing applications such as Microsoft or Google email services.
How can password spraying attacks be prevented?
With a variety of tools, such as MSOLSpray, Ruler, THC-Hydra, Talon and so on, readily available to threat actors, password spraying attacks are relatively easy to execute. Although simple, they yield effective results since many companies still permit weak passwords and password-only logins for their customers and employees.
Listed below are some reliable ways through which you can prevent password spraying attacks.
- Apply brute force prevention on both fields (i.e., Username and Password).
- Use advanced usernames and passwords that are not easy to guess. Protect your organization with credentials stronger than admin and password123!, for example.
- Remove unused accounts with high-level permissions.
- Review permissions regularly and adjust scope as appropriate.
- Salt the hash: Randomize password hashes by adding a random string of letter and numbers (salt) to the password itself. This string should be stored in a separate database and retrieved and added to the password before it’s hashed. By salting the hash, users with the same password have different hashes.
- Encrypt passwords for systems with high encryption rates (preferably with 256-bit encryption). This will make it harder for brute force attacks to succeed.
- Set account lockout policies after a certain number of failed login attempts to prevent credentials being guessed.
- Implement CAPTCHA where lockout is not a viable option.
- Admin-managed applications should force users to change their password upon first login with the default password.
- Enable Two-Factor Authentication (2FA).
- For Azure Active Directory environments, configure Azure AD Password protection to eliminate use of easily guessed passwords, including a globally banned password list that Microsoft maintains and updates.
- Simulate phishing and password attack campaigns in your organization to identify poor cyber hygiene practices. This will enable you to dedicate additional training where needed as well as build a custom list of banned passwords for the organization.
Deliver end-to-end protection for email, accounts and data with Spanning 360
Spanning 360 is the industry’s only enterprise-class, end-to-end protection solution for Microsoft 365 and Google Workspace with advanced capabilities to help prevent, anticipate and mitigate account compromise and data loss caused by phishing, ransomware and malware attacks, human error, malicious behavior, and configuration and sync errors.
Spanning 360 enables you to:
- Prevent: Detect and block even the most sophisticated email threats
- Anticipate: Secure accounts at risk before a data loss occurs
- Mitigate: Quickly find and restore data to its original state in just a few clicks
Click the button below to learn more about the powerful features of Spanning 360.
Learn more about Spanning 360