Cloud and Data Security
CybersecuritySocial Engineering: Definition, Examples, Types of Attacks and How to Prevent Them
More than 90% of cyberattacks rely on some form of social engineering. Learn about social engineering attacks, what to look for, and how to prevent them.
By
Spanning Cloud Apps
13 minute read
What is social engineering?
Social engineering involves psychologically manipulating individuals into performing certain harmful activities or giving away sensitive/private information.
In one of the latest incidents, a group of farm laborers and unemployed youths from a village in India managed to trick sports bettors in Russia to bet on a fake IPL (a professional Twenty20 cricket league) cricket tournament. The scammers streamed bogus cricket matches live over a YouTube channel for over two weeks and took bets on a Telegram channel that they set up. Sound effects downloaded from the internet and an impressionist who could mimic a famous commentator made the fake tournament appear authentic to the remote Russian audience.
This might be a funny story, but the harsh reality is everyone is at risk. Both individuals and businesses are battling against social engineering, struggling to find a way out of this growing menace. Are you one of them? If so, keep reading to find out what social engineering is, how it works, how to spot social engineering attacks and how to better protect your company’s lifeline — data.
What are the origins of social engineering?
The term “social engineers” (sociale ingenieurs) was first introduced by Dutch industrialist J.C. Van Marken in 1894. He believed that just as specialists with technical expertise could solve the problems of machines and related processes (technical issues), social engineers could solve human-related problems, aka social issues. His ideas came from improving the lives of his employees. His factories had schools, libraries, social clubs and so on, that employees and their families could utilize. He also offered insurance funds to his employees. One of his policies included his workers mandatorily saving money for unforeseen difficulties in the future. Van Marken used social engineering as a tool to change the attitude/behavior of his employees.
Unfortunately, unlike Van Marken, some people want to use these techniques to benefit themselves. Social engineering is a highly successful cybercrime technique and is one of the most prevalent cyberthreats that present-day businesses must be aware of. Social engineering is the weapon of choice among cybercriminals because it is much easier to execute and is inexpensive. It is estimated that more than 90% of cyberattacks rely on some form of social engineering.
What are other examples of social engineering in the past?
You may have heard of many of these infamous scams already, but by seeing how varied they can be, we can truly understand the threat social engineering presents to us in person or on the web.
The Nigerian scam, also popularly known as the advance fee scam or 419 scam, is one of the finest examples of social engineering. The scammer would pretend to be a government or bank officer, or a businessman who needs access to an overseas bank account to transfer money trapped in a frozen Nigerian back account, in exchange for a commission. Sometimes, the commission offered can go up to several million dollars to lure the victim. The perpetrator then convinces the victim to send a small amount of money for certain costs associated with the transaction, such as taxes and legal fees. Once the victim sends the money, the scammer would disappear. In certain cases, the scammer would ask the victim to send more money for unexpected costs like increased taxes or bribes to government officials.
In February 2022, a man disguised as a Walmart employee was able to successfully steal several television sets from a Memphis Walmart without being noticed.
Did you ever come across an offer that seemed too good to be true? In 2010, Anthony Lee, a lorry driver from Yorkshire, attempted to sell one of London’s iconic landmarks, the Ritz Hotel. Anthony offered to sell the luxurious hotel for 350 million pounds, which is much less than its actual value. Surprisingly, he was able to trick unsuspecting buyers into depositing 1 million pound before being jailed for the outrageous scam.
Social engineering today, has reached a new level of sophistication. Over the years, social engineering attacks have evolved to become one of the biggest cyberthreats for individuals and organizations alike.
How has technology changed social engineering attacks?
Social engineering in the realm of cybersecurity and information security is the process of manipulating human psychology or behavior, tricking unsuspecting victims into performing certain actions or revealing sensitive information. Once the victim performs the desired action, it creates security gaps for threat actors to slip through. They also use the shared information to gain access to an organization’s network and data, undetected. According to the World Economic Forum (WEF) Global Cybersecurity Outlook 2022 report, social engineering emerged as the second-greatest concern among global cyber leaders, ransomware being their number one concern.
The global pandemic provided the perfect conditions for increased social engineering attacks. The world transitioned from communicating face-to-face to using digital mediums, such as email, video calls, SMS and instant messaging to interact, which are goldmines for cybercriminals. It is no surprise that social engineering threats increased by a whopping 270% in 2021.
Now, with organizations moving to a hybrid work environment, onsite vulnerabilities are coming back. A lower physical presence in the workplace means less “eyes” and physical security from people. IT admins have become too used to servers being “secure” through obscurity, and assume they can leave root passwords unchanged since no one came to the building. Moreover, since the global workforce has been working from home for nearly two years now, most employees do not recognize everyone or even individuals in their own departments. Threat actors looking for opportunities could use “classic” social engineering to break into buildings during smoke breaks or tailgate their way into an office building. This makes plugging in USB drives with malware in computers or other media slots extremely easy.
What weakness does social engineering exploit?
Cybercriminals have found easy methods to exploit weak points in humans rather than finding vulnerabilities in a company’s IT infrastructure. Instead of hacking an organization’s networks and systems, social engineering attacks aim to exploit human nature or qualities such as trust, greed, obedience, kindness, curiosity and so on. Why attack the infrastructure directly when you can simply use people to go through it or around it?
Social engineering attackers or social engineers patiently hope for at least one individual, say, in an organization of 100 employees or 1,000 employees, to commit a mistake. One wrong move — clicking on a malicious link or downloading a malware-infected attachment — is all it takes for the attacker to breach an organization’s security perimeter to steal data or deploy malware. They rely on real communication with employees to convince them to disclose valuable information or act as intended by the perpetrator. The techniques used in social engineering can be simple but highly persuasive. Threat actors may pose as someone that employees trust or entice them with something they want in exchange for something the scammers need. In 2020, cybercriminals used AI to clone the voice of a company’s director, which was used to convince the manager of a UAE bank to transfer $35 million.
What are the different types of social engineering attacks?
Humans are bound to make mistakes, and this also makes social engineering highly successful. Over the years, social engineers have developed new and complex techniques to exploit human error. Many of these methods proved to be fruitful, as seen in the statistics above. Listed below are some common types of social engineering attacks that every business and individual should be wary of.
Phishing
Phishing is the most prevalent and common type of social engineering attack. This method attempts to exploit human error using malicious emails, attachments and links to collect credentials, spread malware or perform a variety of insidious actions. Malicious emails may seem to have come from the IT department of a company, requesting its employees to change their passwords immediately. Such emails may seem legitimate and can be harder to detect. In a recent cybersecurity incident, threat actors managed to hack an employee’s email belonging to Kaiser Permanente, the largest nonprofit health plan provider in the United States. The event led to the disclosure of sensitive health information of about 70,000 patients. Here is an example of a phishing email: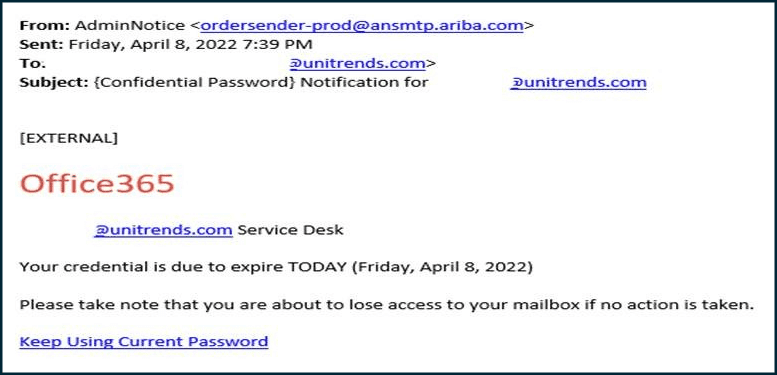
Spear phishing
Similar to phishing, spear phishing is an email-based scam, but is more targeted and personalized. It targets a specific individual or company rather than sending mass emails to a group of people. This tactic involves prior research on the victim — the victim’s name, position in the company, etc., — before launching an attack. Cybercriminals then use the information gathered to craft attractive emails to entice the victim. This increases the probability of the victim opening the malicious email or clicking on the infected link. These emails are designed in such a way that they appear to be from a trustworthy source, from someone the victim knows or trusts.
SMiShing
SMS phishing or SMiShing, is a type of phone text message used by cybercriminals to collect valuable information, request fund transfers or gift cards, and even distribute malware. These text messages lure recipients into responding because they often appear to be a message from an executive manager within an organization.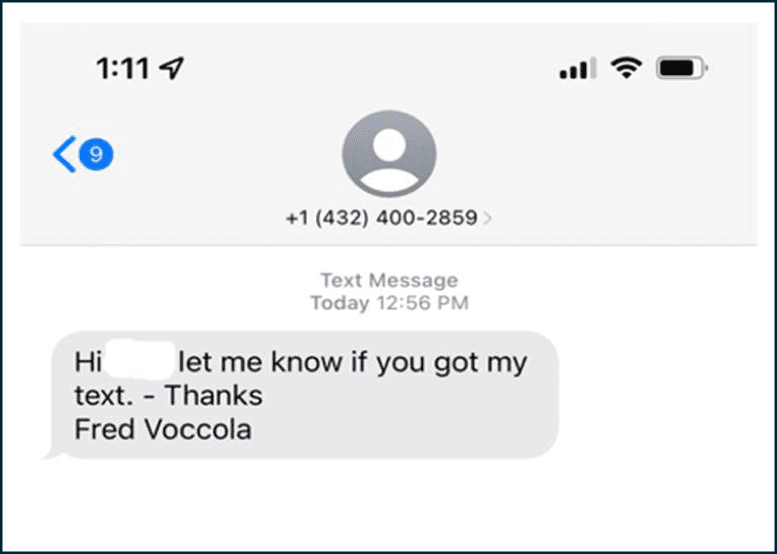
Vishing
Vishing, also known as voice phishing, is another form of SMiShing, but this phone-based attack uses voice call/messaging. The goal is to gather victims’ personal information, credit card numbers or credentials. The scammer can then use the information to perform identity theft. Here is a video by Kevin Roose from Future Technology, featuring social engineering hacker Jessica Clark, demonstrating how easy it is for hackers to execute social engineering.
Tailgating
Tailgating is another form of social engineering where the fraudster tries to gain entry into a restricted area or building by simply walking behind someone who has authorized access. Tailgating can be effective in small or midsized businesses. However, it can be difficult in large corporations where everyone entering the office must swipe their cards or punch in access codes.
Baiting
This is another variant of social engineering where threat actors attempt to exploit the victim’s greed or curiosity by making a false promise. For instance, threat actors can use a USB drive (malware-infected) tagged “employee payroll or project details” as bait to lure unwitting victims. Attackers will leave the infected USB drive in a strategic area where it can be easily seen. If an unsuspecting victim picks up the bait and connects it to their computers out of curiosity, malware will be installed.
Quid pro quo
Quid pro quo means “something for something” in Latin. Just like its name, this method of social engineering involves seeking sensitive or personal information in exchange for something, usually in the form of a service. Often, the perpetrator would pretend to be a customer support executive or a technical expert and target unwitting victims, promising them a service in return for confidential data.
Pretexting
Pretexting attacks rely on fabricated stories — a good pretext — to trick individuals into disclosing confidential data. The perpetrator impersonates a co-worker or an authoritative figure to build trust and gather sensitive information from the victim. Since pretexting emails appear to be from someone from within the organization or someone the victim knows, it is easy for the victim to assume the emails are legitimate and safe. This makes pretexting a highly successful social engineering technique.
Scareware
Scareware is a social engineering technique that uses pop-up ads to exploit fear in humans. Social engineers use false alarms or bogus warnings to create panic in users’ minds. It aims to trick users into believing that they must buy or download certain software to address fictitious cybersecurity issues. In reality, the software would do more harm than good since it is often malware infected.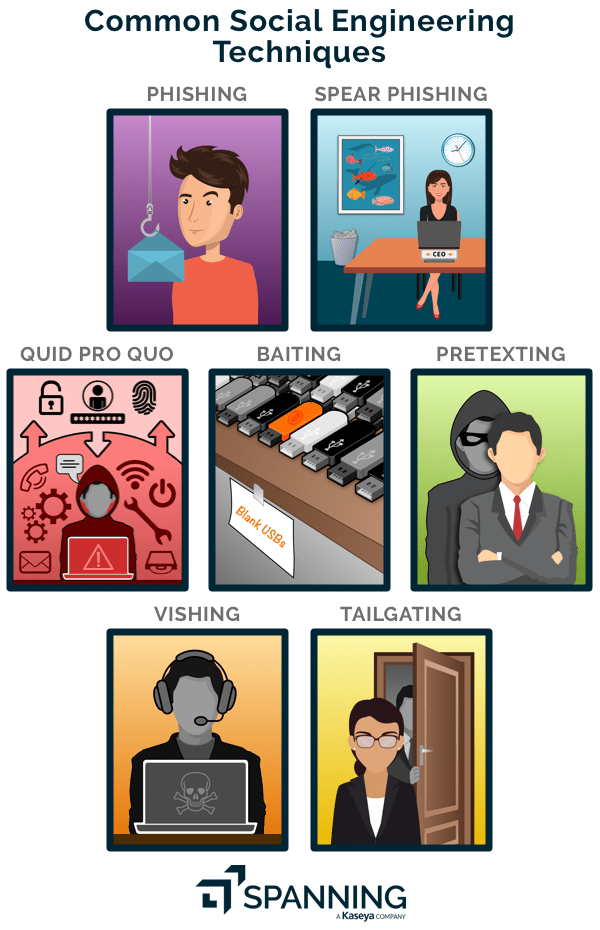
What are some warning signs of social engineering?
There are many forms of social engineering attacks. They use compelling stories and are creatively designed, which makes them extremely difficult to spot. Despite using antivirus or spam filters, malicious emails can still enter employee inboxes.
Here are a few telltale signs that will help you recognize these attacks.
- Receiving an unusual message from your colleague, manager or someone you know.
- Getting deals that are too good to be true.
- Receiving a request that offers you something you want in exchange for sensitive company information.
- Receiving an unusual request to perform an action that has never been done before and threatening you of dire consequences if the request is ignored.
- Receiving a request to do something urgently.
- Receiving emails, phone calls, text or voice messages from unknown numbers.
- Receiving emails, phone calls, text or voice messages to verify your information.
- Receiving email requests to change passwords immediately.
- Receiving emails warning you of account lockout or closure.
How is social engineering prevented?
Social engineering attacks are highly successful and are here to stay. There is no one-size-fits-all solution to prevent these attacks. However, you can manage and mitigate the risks by taking proactive steps.
Make security a part of your corporate culture
Fighting cybercrime is an ongoing effort. Encourage your employees to report security incidents or suspicious instances to your security team as soon as they occur or are discovered. Develop security policies and an incident response plan that detail how you would respond to a cybersecurity incident, your incident response team, who to communicate to, your action plan and so on. This will help to minimize the damage as well as contain the situation efficiently.
Educate your employees
The best way to deal with a problem is by generating as much information as possible and being aware of it. Effective training programs coupled with tests to assess the efficacy of the courses will be a first, good step toward empowering your employees and mitigating risks associated with social engineering.
Use two-factor or multifactor authentication
Passwords alone are no longer sufficient to deter today’s complex cyberthreats. Having a multilayered strategy is crucial to reducing cyber-risk and securing accounts and data effectively. The use of two-factor or multifactor authentication makes protecting your company’s accounts and data easier by adding another layer of security.
Implement cybersecurity tools
Using cybersecurity solutions to improve your organization’s security posture is a no-brainer in today’s threat landscape. Your company must leverage antivirus, anti-malware, anti-phishing software and user credentials monitoring programs, to name a few, to thwart social engineering in its tracks.
Back up data
Protect your data with a layered defense. When all else fails, be ready to recover. Data protection is an important aspect of your company’s business continuity strategy. Data backups are essential for quick recovery from a cybersecurity incident. Having a clean copy of your organization’s mission-critical data will help minimize downtime and disruptions to your business.
Safeguard your data from social engineering with Spanning 360
Businesses being breached despite having security systems in place is not new. When everything seems to be going wrong, backup is your last resort. Your backup solution will define how quickly you can get back up and running after a data loss incident.
Spanning 360 is the industry’s only enterprise-class, end-to-end protection solution for Microsoft 365 and Google Workspace, with advanced capabilities to help prevent, anticipate and mitigate account compromise and data loss. Its purpose-built, cloud-native technology is remarkably easy to install, manage and use. You can start protecting your business-critical data in a matter of minutes. Spanning 360 requires no hardware and is fully automated, enabling end-user functionality and simplified administration.
Schedule a demo today to see Spanning 360 live in action.
Schedule a Demo