Cloud and Data SecurityXML External Entity (XXE) Attacks — Web-based Application Security, Part 5
XML External Entity (XXE) attacks are a form of injection attack that target weak XML parsers with the goal of exposing confidential information that should typically not be accessible. Learn how they work and how to protect against them.
By
Shyam Oza
3 minute read
Consider this:Your website crashes due to a Denial of Service (DoS) attack. And when you get to the bottom of it, you find that it was caused by an exponential amount of “LOL”s completely draining your resources. Not amusing in the least! You’re a victim of the infamous Billion Laughs Attack, a type of an XML External Entity (XXE) attack.
In this blog series, we spotlight one critical web app vulnerability with pointers to secure your organization (past spotlights have included Open Redirection Vulnerability, Cross-Site Forgery, Cross-Site Scripting (XSS) Vulnerability and SQL Injection). Read on as we analyze the culprit behind the “XML bomb” attack described above – XML External Entity (XXE) vulnerability.
What is an XXE Attack?
According to web-app security watchdog, OWASP, “*An XML External Entity attack is a type of attack against an application that parses XML input. This attack occurs when XML input containing a reference to an external entity is processed by a weakly configured XML parser.”*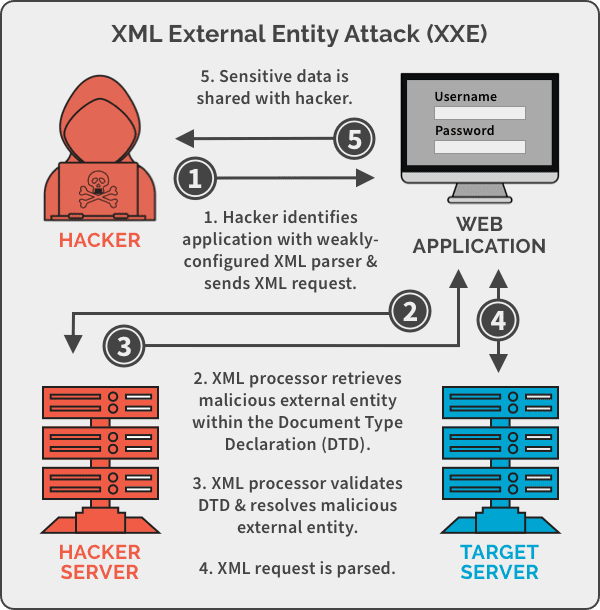 The reason why XXE makes it to OWASP’s Top 10 Web App Security Vulnerabilities is largely due to the immense popularity of its underlying “vector” – XML. XML is an extremely popular markup language that is used extensively by websites. It is the default standard for exchanging messages between enterprise applications in a Services Oriented Architecture.
The reason why XXE makes it to OWASP’s Top 10 Web App Security Vulnerabilities is largely due to the immense popularity of its underlying “vector” – XML. XML is an extremely popular markup language that is used extensively by websites. It is the default standard for exchanging messages between enterprise applications in a Services Oriented Architecture.
XML’s main advantages are its extensibility, acceptance (storage) of any type of data and it being an accepted public standard. However, within its advantages lie its susceptibilities, too. XML is accepting of loosely defined external entities that can access local or remote content via a declared system identifier. If that system identifier contains tainted data or is parsed through a weak XML parser, the XML processor may expose confidential information that should typically not be accessible. This loophole can be exploited, leading to data theft, data corruption, server-side request forgery, malicious code execution, network attacks, and DoS attacks.
An XXE Attack in Action
Consider the example we started with — **the Billion Laughs.**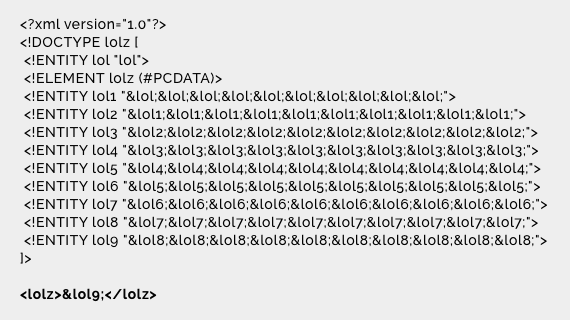 The XML parser will only see the lolz root element. However, that contains string entities that have an increasing number of “lol”s. When all 9 entity expansions have been processed, it will actually contain 109 “lol”s that will consume almost 3 GB of memory, thus exhausting your resources and leading to a DoS attack.
The XML parser will only see the lolz root element. However, that contains string entities that have an increasing number of “lol”s. When all 9 entity expansions have been processed, it will actually contain 109 “lol”s that will consume almost 3 GB of memory, thus exhausting your resources and leading to a DoS attack.
To understand how XXE can be used to access confidential data, let’s look at this example: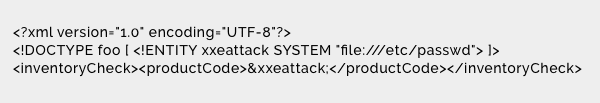 Here, xxeattack can pull the entire list of user ids and passwords via inventoryCheck which is supposed to be an inventory checking application.
Here, xxeattack can pull the entire list of user ids and passwords via inventoryCheck which is supposed to be an inventory checking application.
Preventing an XXE Attack
A few pointers to secure your web apps from XXE attacks:
- Parse the Parser: Essentially, XXE is a form of injection attack that attacks weak XML parsers. Hence, a basic defense is to check your application’s XML parsing library for XML features that can be misused, and disable them. In particular, disable DTDs (External Entities), as detailed here. Also, check that your XML processors are patched.
- Verify Inputs: Verify that file uploads are XSD validated, and only whitelisted URLs are allowed.
- Test via Code: Don’t underestimate manual code reviews. Identify and test for XXE attacks via API calls. Validate user inputs prior to it being parsed by the XML parser.
- Remember the Basics: Ensure that network monitoring tools and application firewalls are updated.
Stay tuned for the next part of our Web Application Security Series where we examine another sensitive vulnerability.
Read More About Cloud & Data Security