Microsoft has taken extensive measures to alleviate the risks of data loss within Microsoft 365 and has put safeguards in place to ensure your data's safety from any fault on their behalf. However, it's important to understand that this protection operates under Microsoft's Shared Responsibility Model.
Under this model, Microsoft assumes responsibility of physical security at their data centers, as well as data storage replication and redundancy. The model also clearly states that your organization retains the ultimate responsibility for data protection. Microsoft affords no protection from the actions of your users and threats beyond their control that constitute the majority of data loss events.
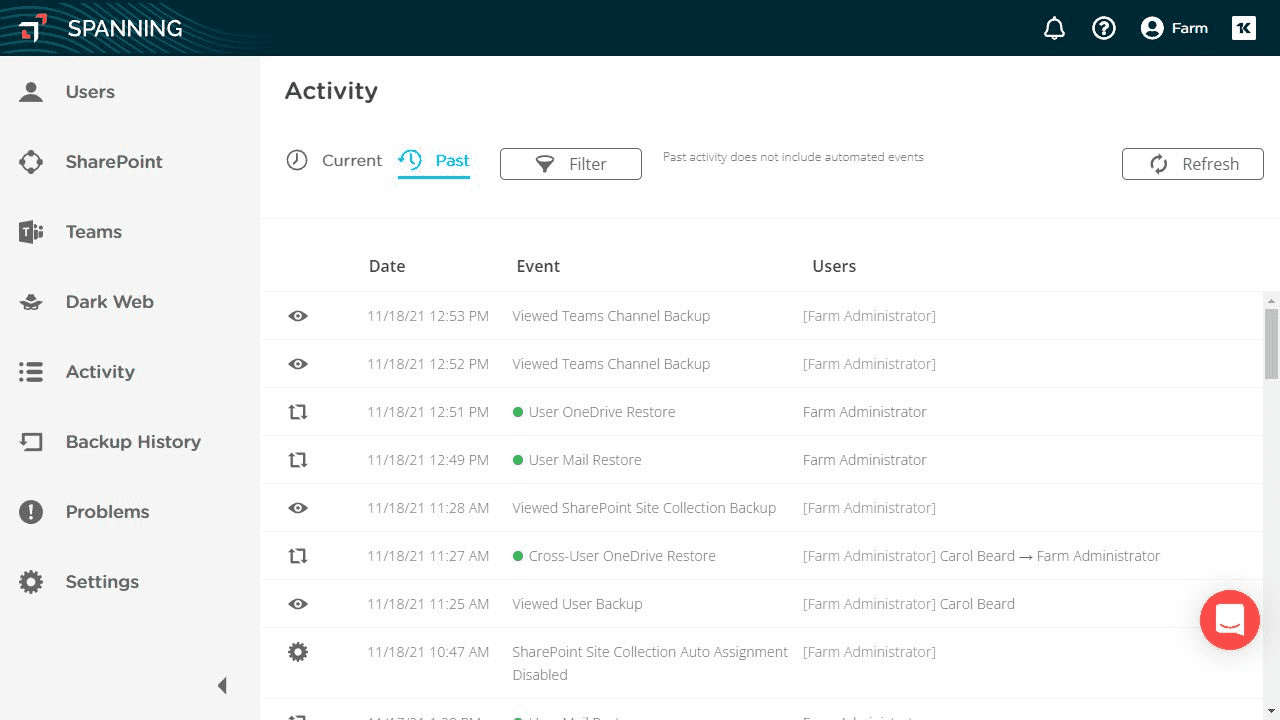
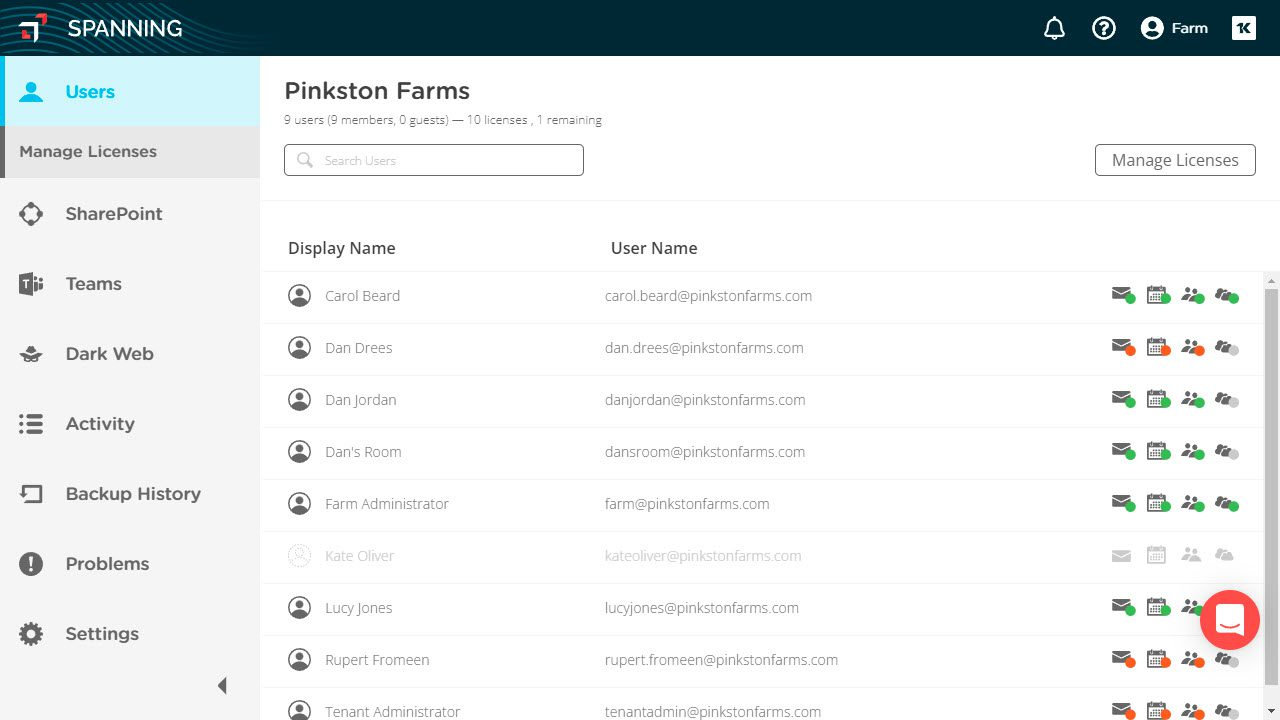
The bottom line is that the safety of your Microsoft 365 data is your responsibility. The Microsoft Services Agreement states they “recommend that you regularly backup Your Content and Data that you store on the Services or store using Third-Party Apps and Services.” This is why it's important to have a third-party backup and recovery solution, such as Spanning, for your data.