[On-Demand Webinar] Beyond Collaboration: Continuity With Google Workspace Backup
Watch the Spanning on-demand webinar to learn how to protect Google Workspace data confidently. [...]
[On-Demand Webinar] Mastering Salesforce Backup
Watch the Spanning on-demand webinar to learn how to unlock the power of Salesforce while ensuring the safety and resilience of your business-critical [...]
[Checklist] 5 Steps to Safeguard Student Data
Get an in-depth look into the steps that educational institutions like yours can implement to protect your critical student data. [...]
Build Your Business Case for Salesforce Backup
This is a step-by-step guide for IT pros to effectively build a business case for Salesforce backup. Download the guide now. [...]
Build Your Business Case for Microsoft 365 Backup
This infographic shows the three major risk drivers in your IT organization and how to overcome them. [...]
[On-Demand Webinar] Navigating the Future: 2024 — The Year of IT Resilience
Watch the Spanning on-demand webinar to learn about the strategies to empower your business to thrive in the face of uncertainty. [...]
Build Your Business Case for Google Workspace Backup
This infographic shows the three major risk drivers in your IT organization and how to overcome them. [...]
[Infographic] Unlock Resilience in Every Byte
This infographic shows the three major risk drivers in your IT organization and how to overcome them. [...]
[On-Demand Webinar] Ransomware Preparedness With Spanning
Watch this roundtable session where our experts shared tips and tricks to identify and mitigate cyber-risks your organization faces. [...]
[Datasheet] FLEXspend for Spanning
Learn how FLEXspend for Spanning seamlessly replaces any unneeded Spanning Backup solution with another technology from Unitrends or Spanning that ali [...]
The Summer 2023 Continuity Cookbook
The summer is here! Get ready to liven up your spirits and enjoy a stress-free holiday. [...]
SaaS Backup Buyer’s Guide LIVE Webinar
Watch this roundtable session where our experts shared tips and tricks to identify and mitigate cyber-risks your organization faces. [...]
[eBook] IT Risks: Backup and Recovery Blueprint
This eBook provides a blueprint for organizations to achieve ICT Readiness for Business Continuity (IRBC) and continue operating amidst an IT disaster [...]
Infographic: The Three Major IT Risk Drivers
This infographic shows the three major risk drivers in your IT organization and how to overcome them. [...]
The Three Major Risk Drivers in Your IT Organization
This eBook provides deep insights into your IT organization's three major risk drivers and how to overcome them. [...]
[Checklist] Combat IT Risks for Your Business With Confidence
Discover how to overcome the major risk drivers in your IT ecosystem confidently with our complete, all-in-one SaaS backup and recovery solution. [...]
[Roundtable] Make Identifying & Mitigating Cyber-Risks a Sure Thing
Watch this roundtable session where our experts shared tips and tricks to identify and mitigate cyber-risks your organization faces. [...]
[Webinar] Google Workspace Power Demo
Join our power demo to learn how to install, deploy and restore all Google Workspace files, folders and emails. [...]
[Webinar] Microsoft 365 Backup Power Demo
This condensed 20-minute live Power Demo will help you discover the robust capabilities and crucial elements of Spanning Backup for Microsoft 365. [...]
[On-Demand Webinar] 3 Must-Haves to Secure Student, Systems & SaaS Data
Join our SaaS backup experts to learn how educational institutions can secure their systems, student data and SaaS applications. [...]
The ‘Cyber ASaaSin’ Manual
Read this manual to gain insights into how Spanning can be the “Cyber ASaaSin” required to identify the SaaS data enemies and stop them in their t [...]
On-Demand Webinar- Cyberthreats to Look Out for in 2023
Watch this on-demand webinar to learn the best practices to keep your users off phishing hooks this holiday season. [...]
Reduce OpEx and streamline compliance with Spanning Backup 1-year retention
Learn more about the key features, advanced capabilities and benefits of Spanning 360 in our data sheet. [...]
The Essential Eight Security Obligations
This whitepaper gives insights into the state of preparedness of businesses in the ANZ region for fulfiling the region’s new cybersecurity obligatio [...]
On-Demand Webinar- Phishing Defense for Holiday Season
Watch this on-demand webinar to learn the best practices to keep your users off phishing hooks this holiday season. [...]
Tech Trends & Insights 2023 Survey Findings: The State of IT Security
This infographic explores responses from over 650 IT professionals worldwide to learn about their approach to cybersecurity. [...]
Tech Trends and Insights: State of BCDR
This infographic explores responses from over 650 IT professionals worldwide to learn about their approach to BCDR. [...]
Tech Trends and Insights: State of Cyberattacks
This infographic shows how cyberattacks and data breaches are affecting today’s hybrid cloud environments. [...]
Tech Trends & Insights 2022/2023 Survey Report
Earlier this year, we surveyed more than 650 IT professionals worldwide to learn about technology-related priorities, concerns, and how their approach [...]
Spanning Continuity Cookbook 2022 – Holiday Edition
Cook up your SaaS backup plans and your next holiday meal with some exciting recipes from our SaaS Continuity Cookbook. [...]
Turning Data Loss Tricks into Recovery Treats
Watch the Spanning on-demand webinar to learn how to safeguard your data by developing a robust cyber resilience strategies no matter your business si [...]
ESG Research: SaaS Data Protection – A Work in Progress
This eBook presents a new way to gain insights into the trends and requirements for successful data protection strategies for SaaS environments. [...]
The Complete SaaS Backup Buyer’s Guide
This buyer’s guide highlights best practices for protecting your SaaS data and provides key criteria for selecting the best backup solution for your [...]
Five Actionable Lessons From Recent Top Cybersecurity Incidents
Get the eBook to learn about the top cybersecurity incidents that occurred recently and five actionable lessons from these events. [...]
Spanning SaaS Backup and Recovery Survey Report 2022
Spanning surveyed IT leaders in more than four different continents to understand the current and future landscape of SaaS backup approaches. Get the [...]
Restoring Your Microsoft 365 Data With Spanning Backup
Watch the webinar recording to see how Spanning provides enterprise-grade backup and recovery for Microsoft 365. [...]
Phishing and Account Compromise – Fighting the Social Engineering Threat to Google Workspace
Watch the Spanning on-demand webinar to learn how to overcome social engineering attacks with the right tools and strategies. [...]
Data Retention Limits in Microsoft 365 and Google Workspace
This infographic compares data retention policies for Microsoft 365 and Google Workspace to show when and why your SaaS data is no longer available. [...]
Best Office 365 Backup Solutions — DCIG Report
The 2021-22 DCIG TOP 5 Office 365 Online SaaS Backup Solutions report highlights the five best SaaS backup solutions to protect organizational data st [...]
Building the Business Case for Microsoft 365 Backup
Watch the Spanning on-demand webinar to find out how Spanning 360 reduces the data protection burden on Microsoft 365 administrators. [...]
Spanning Backup for Google Workspace Evaluation Criteria Checklist
See how Spanning Backup for Google Workspace stacks up against the competition with the evaluation checklist. Learn more. [...]
Spanning Backup for Microsoft 365 Evaluation Criteria Checklist
See how Spanning Backup for Microsoft 365 stacks up against the competition with the evaluation checklist. Learn more. [...]
Spanning Backup for Salesforce Evaluation Criteria Checklist
See how Spanning Backup for Salesforce stacks up against the competition with the evaluation checklist. Learn more. [...]
Reducing the Data Protection Burden on Google Workspace Administrators
Watch the Spanning on-demand webinar to find out how to effectively protect your Google Workspace accounts, emails and data. [...]
Reducing the Data Protection Burden on Microsoft 365 Administrators
Watch the Spanning on-demand webinar to find out how Spanning 360 reduces the data protection burden on Microsoft 365 administrators. [...]
Reducing the Data Protection Burden on Salesforce Administrators
Watch the on-demand webinar to find out how Spanning Backup reduces the data protection burden on Salesforce administrators. [...]
Google Workspace Security and Data Protection – What’s Included and What’s Not?
The Google Workspace Security and Data Protection eBook highlights the threats, explains the security and data protection features included in each Go [...]
Microsoft 365 Security and Data Protection – What’s Included and What’s Not?
The Microsoft 365 Security and Data Protection eBook highlights the threats, explains the security and data protection features included in each Micro [...]
Phishing and Account Compromise – Fighting the Social Engineering Threat to Microsoft 365
In this webinar, we detail the steps involved in building a business case for an Office 365 or Google Workspace backup solution while providing an ROI [...]
Best Practices for Google Workspace Business Continuity Ebook
This eBook presents a new way of looking at business continuity, based on the SaaS model and optimized for Google Workspace. [...]
Best Practices for Salesforce Business Continuity
This eBook presents a new way of looking at business continuity, based on the SaaS model and optimized for Microsoft 365. [...]
Best Practices for Microsoft 365 Business Continuity Ebook
This eBook presents a new way of looking at business continuity, based on the SaaS model and optimized for Microsoft 365. [...]
Building the Business Case for Office 365 and Google Workspace Backup
In this webinar, we detail the steps involved in building a business case for an Office 365 or Google Workspace backup solution while providing an ROI [...]
Spanning 360: Product Datasheet
Learn more about the key features, advanced capabilities and benefits of Spanning 360 in our data sheet. [...]
Backup & Brew: What’s New With Spanning (March, 2022)
Watch the on-demand webinar to learn about Spanning’s new features and capabilities to bolster your SaaS data protection strategy. [...]
Best Practices for Google Workspace Business Continuity
Dave Wallen and Shyam Oza present a new way of looking at business continuity, based on the SaaS model and optimized for Google Workspace. [...]
Cities With the Most Technology Jobs Per Capita
This list ranks the U.S. metros with the highest number of technology jobs per capita (largest share of employment in computer and math occupations). [...]
The Best-Paying U.S. Cities for IT Administrators
This list examines which metro areas offer the best salaries for IT admins, based on median wage & employment data from the U.S. Bureau of Labor Stati [...]
People Problems — Protecting Your Salesforce Organization From Human Error and Malicious Activity
Salesforce data faces constant people problems — malware attacks, malicious behavior, configuration errors — the list goes on and on. Learn how to [...]
The Largest Data Breaches in U.S. History
This list explores the 10 largest data breaches of U.S. companies based on the total number of records exposed, regardless of record type. [...]
Don’t Let an Ass Jack Your SaaS: Understanding SaaS Data Threat Profiles
Jackasses like these are the prime reason why over 75% of businesses using Google Workspace, Office 365, and Salesforce suffer a data loss incident ea [...]
Simple, Easy-to-Use Office 365 Backup
Spanning makes backup seamless with a quick, easy setup that's accompanied by an intuitive interface. See how easy it is to use Spanning Backup for Of [...]
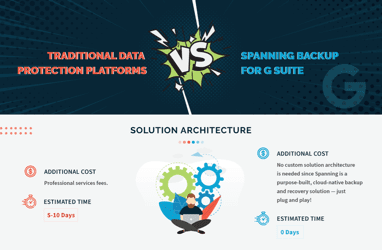
Traditional Data Protection Platforms vs. Spanning Backup for Google Workspace
An infographic comparing the cost & complexity of procurement, installation, configuration, management, training, and usage of Spanning Backup for Goo [...]
Restore OneNote Backup: Spanning Backup for Office 365
Spanning Backup for Office 365 protects Microsoft OneNote Notebooks. This video details the steps to get your OneNote content back to where you need i [...]
Don’t Let an Ass Jack Your SaaS: Understanding Office 365 Data Threat Profiles
Jackasses like these are the prime reason why over 75% of businesses using Office 365 suffer a data loss incident each year. [...]
Don’t Let an Ass Jack Your SaaS: Understanding Salesforce Data Threat Profiles
Jackasses like these are the prime reason why over 75% of businesses using Salesforce suffer a data loss incident each year. [...]
Don’t Let an Ass Jack Your SaaS: Understanding Google Workspace Data Threat Profiles
Jackasses like these are the prime reason why over 75% of businesses using Google Workspace suffer a data loss incident each year. [...]
Dark Web Monitoring Data Sheet – Spanning Backup for Google Workspace
Spanning Dark Web Monitoring for Google Workspace alerts administrators of compromised or stolen employee credentials, enabling them to take proactive [...]
Salesforce Data Recovery: Evaluating Your Options
The Salesforce Data Recovery Service is being discontinued. What does this mean for you? In this recorded webinar, we explore your Salesforce data bac [...]
Dark Web Monitoring for Office 365 — Video Overview
Dark Web Monitoring alerts Office 365 administrators when their employee's emails and passwords have been compromised enabling them to take proactive [...]
Office 365 Shared Responsibility Model — On-Demand Webinar
SaaS vendors such as Microsoft operate based on a shared model of responsibility – they provide application availability, redundancy, and fault-tole [...]
Dark Web Monitoring: Feature Datasheet
Optional Dark Web Monitoring alerts Office 365 administrators when their employee's emails and passwords have been compromised enabling them to take p [...]
The ROI of Microsoft Office 365 Backup
Decision makers are often skeptical of Office 365 backup. They rarely can wrap their heads around a solution that doesn’t increase their margins. Th [...]
The ROI of Google Workspace Backup
Decision makers are often skeptical of Google Workspace backup. They rarely can wrap their heads around a solution that doesn’t increase their margi [...]
The Right Way to Secure Your SaaS Backup
This infographic highlights the many causes of data loss that often go overlooked and illustrates four key points that companies need to consider in o [...]
Securing Your SaaS Backup — The What, Where, How, and Who
Relying on Google Workspace and Office 365 for protecting your business-critical data isn’t enough. The right backup and recovery solution is needed [...]
Dennis Publishing User Story: Spanning Backup for Google Workspace & Salesforce
Dennis Publishing, a much loved premium content publisher in the UK and US market, stays ahead of the curve by being relentlessly inventive in terms o [...]
Cloud Data Protection Strategies: Protecting Data To and In the Cloud — ESG Report
The broad adoption of cloud services as a source of business-critical data is placing the onus on data owners to deliver on data protection SLAs of da [...]
Improving Governance in Office 365
Security and compliance concerns top the list of challenges organizations face when migrating to the cloud. In this report, “Improving Governance in [...]
Office 365 Security & Compliance Practices — CollabTalk Report
A new research report reveals the major pain points for organizations when managing security and compliance governance for Microsoft Office 365. Altho [...]
Westland Real Estate Group User Story: Spanning Backup for Google Workspace
Westland Real Estate Group, a 50-year old Real Estate Company, trusts Spanning Backup for Google Workspace to protect their data against ransomware an [...]
A Best Practices Guide: Realizing the Promises of Google Workspace for Education
School districts, colleges and universities around the globe are adopting Google Workspace for Education. In this whitepaper, you’ll learn more abou [...]
Spredfast User Story: Spanning Backup for Salesforce
Data drives Spredfast’s business. Protecting that data is critical and that’s why Stephanie Herrera chose Spanning Backup for Salesforce based on [...]
Salesforce Sandbox Seeding: Spanning Backup for Salesforce
Learn how to seed sandboxes with Spanning Backup for Salesforce's cross-org restore functionality. [...]
Cybersecurity and Risk Awareness — Spanning Report
Spanning commissioned a survey of over 400 U.S. workers across a range of industries, including education, government and healthcare, to determine awa [...]
On-Page Restore: Spanning Backup for Salesforce
In this video, learn how to use Spanning's On-Page Restore feature to restore field-level data back into your Salesforce records. [...]
Understanding the Difference between Google Vault and Spanning Backup
Learn the differences between backup and recovery solutions and Google Vault in this paper that will help you examine your business needs and guide yo [...]
Catholic Education Diocese of Wilcannia-Forbes | Spanning Backup for Google Workspace
The Wilcannia-Forbes Catholic Education Office is part of a consortium with other Australian dioceses’ Catholic Education Offices. Their IT team dec [...]
Spanning Product Line Overview
Learn about our backup and recovery solutions for Office 365, Salesforce and Google Workspace, and why Spanning Backup is the right choice to protect [...]
CORE Education | Spanning Backup for Google Workspace
Natural disasters are near impossible to predict and are difficult to plan for. After the devastating Christchurch Earthquakes in 2011 that caused mas [...]
Preventing a Ransomware Disaster
Learn how Spanning Backups offers a second line of defense against ransomware, saving your business money and the stress of having to negotiate with c [...]
East Coast Migrant Head Start Project User Story: Spanning Backup for Office 365
When ECMHSP transitioned from on-premise email, they needed a dependable solution for Microsoft Office 365 email restoration. Since 2015, they have co [...]
Distilled User Story: Spanning Backup for Google Workspace
After a couple of issues with accidental deletion of individual documents, Distilled realized that the possibility of significant data loss is just no [...]
Salesforce Backup — Product Demo Video: Spanning Backup for Salesforce
In this video, we show you how Spanning Backup for Salesforce works, including how to easily monitor the status of your Salesforce backups, how to res [...]
Restore Office 365 Mail, Calendar & OneDrive Data: Spanning Backup for Office 365
In this video, learn how to restore backed up Office 365 Mail, Calendar, and OneDrive data back into your user's live accounts. [...]
Google Workspace Backup Installation & Configuration — Demo Video: Spanning Backup for Google Workspace
In this video, learn how to install and configure Spanning Backup for Google Workspace. Start protecting your Google Workspace users with daily, auto [...]
Spanning Backup for Salesforce Product Tour
In this video, learn how Spanning Backup for Salesforce can protect your Salesforce data, and how you can restore your backed up data or metadata dire [...]
What is Spanning Backup? — Learn More About Us
Jeff Erramouspe, CEO of Spanning, details what Spanning Backup is, and what makes the service so reliable. [...]
How to Install Spanning Backup for Google Workspace in Under a Minute
Install a Spanning Backup for Google Workspace free trial in under a minute with this quick video! [...]
Getting your cloud strategy on solid ground: Protect data in cloud apps with PHI
If your organization manages e-PHI in cloud applications, the information in this whitepaper is key to keeping your organization compliant and product [...]
Salesforce Metadata Backup & Restore: Spanning Backup for Salesforce
Learn how to restore backed up metadata into your live Salesforce org with Spanning Backup for Salesforce. [...]
Office 365 PowerShell Module — Assigning Licenses: Spanning Backup for Office 365
Learn how to use our example PowerShell Module that leverages our public Rest API to upload a CSV file to mass-assign Spanning Backup licenses. [...]
Restore Specific Fields in Bulk Restore
In this video, we'll show you how to restore specific fields back into your live Salesforce environment using Spanning Backup for Salesforce. [...]
Google Drive Cross-User Restore: Spanning Backup for Google Workspace
In this video, we'll show you how to restore backed up Google Drive data from one user into another user's account with Spanning Backup for Google Wor [...]
Spanning Backup for Salesforce: Installation & Configuration
Learn how to install and configure Spanning Backup for Salesforce for your organization in just 5 minutes. Get detailed instructions in this video. [...]
Spanning Backup for Office 365: Installation & Configuration
Learn how to install & configure Spanning Backup for Office 365 in your tenant in just 6 minutes. We'll walk you through each step in this detailed vi [...]
SharePoint Backup — Demo Video: Spanning Backup for Office 365
Learn how to protect SharePoint document library contents in Team Sites, Group Sites & Microsoft Teams with Spanning Backup for Office 365 SharePoint [...]
Office 365 Backup — Product Demo Video: Spanning Backup for Office 365
Protect your SharePoint, OneDrive, Mail, and Calendar data with Spanning Backup for Office 365. Take a tour of our intuitive user interface. [...]
Spanning Backup for Salesforce: Export Updated or Deleted Records
Learn how to use Spanning Backup for Salesforce to export backed up Salesforce data, from any point in time. Watch the video tutorial. [...]
Install Office 365 Backup in 90 Seconds: Spanning Backup for Office 365
Start protecting your Office 365 data in less than a few minutes. In this video, we walk you through the incredibly easy process to install and config [...]
Ransomware Recovery — Demo Video: Spanning Backup for Google Workspace
Spanning Backup for Google Workspace protects your organization from Ransomware attacks by automatically backing up your Google Drive data, including [...]
Team Drives Backup — Demo Video: Spanning Backup for Google Workspace
Spanning Backup for Google Workspace now offers enterprise-grade data protection for Team Drives, providing daily, automated and on-demand backups, wi [...]
Spanning Backup for Google Workspace Data Sheet
Learn about the features, benefits, and capabilities of Spanning Backup for Google Workspace. [...]
Spanning Backup for Salesforce: Overwrite Field Values
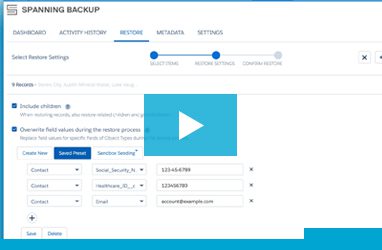
Learn how to overwrite Salesforce field values, such as objects owned by inactive users, or sensitive data, when performing a bulk restore with Spanni [...]
Dell EMC User Story: Spanning Backup for Salesforce
The world's top provider of data protection solutions trusts Spanning to protect critical Salesforce data. Find out why you should, too. [...]
Spanning Backup for Salesforce: Metadata Comparison
Tired of manually comparing metadata when preparing Salesforce restores? See how the Metadata Comparison feature speeds up the process for Salesforce [...]
InZone Industries User Story: Spanning Backup for Office 365
As far as InZone Industries is concerned, there’s no better solution for backing up Office 365 data than Spanning Backup for Office 365. [...]
Google Workspace Backup — Product Demo Video: Spanning Backup for Google Workspace
In this video, we show you how Spanning Backup for Google Workspace works, including how to correct problems with and monitor your Google Workspace ba [...]
End User Training — Demo Video: Spanning Backup for Office 365
Welcome to Spanning Backup for Office 365! Start protecting your Office 365 data by following along in this tutorial. [...]
Spanning Backup for Google Workspace: Full Account Export for End Users
Learn how end users can export their backed up Google Workspace data out of Spanning to their local hard drive. [...]
Complying with SaaS Data Management Principles: Australia and New Zealand
Review the key considerations and primary regulatory issues that organisations must consider as they prepare to adopt services such as Microsoft Offic [...]
Data Disaster Recovery — Demo Video: Spanning Backup for Salesforce
Learn how to perform a full Salesforce org restore with Spanning Backup for Salesforce in the event of a data disaster across your Salesforce org. [...]
Spanning Backup for Salesforce: Packaged Restore
Introducing the 'Packaged Restore' feature of Spanning Backup for Salesforce. Learn how to upload a CSV of object IDs of multiple object types to all [...]
3-Step Guide to SaaS Data Protection
Moving critical data from on-premises apps to cloud-based apps like Salesforce, Office 365, or Google Workspace? Follow these steps to ensure that you [...]
3-Step Guide to Protecting Data in Office 365
You’ve made the move to Office 365 to reap the benefits of the cloud. Now, to ensure business continuity and to meet compliance demands you need to [...]
3-Step Guide to Protecting Data in Salesforce
If your organization lost critical Salesforce data & metadata, how would you restore it? Learn about the benefits of using a third party backup soluti [...]
3-Step Guide to Protecting Data in Google Workspace
Do you know the most common threats to your Google Workspace data? Download the 3-Step Guide to find out the best solution for protecting your Google [...]
BBH Global User Story: Spanning Backup for Google Workspace
Learn how Spanning Backup for Google Workspace gave BBH the confidence to step up the timeline for moving all its business teams’ data to Google Wor [...]
Catholic Education Diocese of Parramatta | Spanning Backup for Google Workspace
Read how the Catholic Education Diocese of Parramatta successfully addressed backup, restore and compliance challenges with Spanning Backup for Google [...]
Microsoft 365 Backup: The Definitive Guide
Now that you’ve found the perfect productivity solution in the cloud, it’s time to get to know your options for keeping your data in Office 365 sa [...]
SThree User Story: Spanning Backup for Salesforce
Read how SThree, a leading global recruitment firm, uses Spanning Backup for Salesforce to help keep the company focused on business instead of backup [...]
Solution Overview: Spanning Backup for Healthcare
If you're managing healthcare data and e-PHI in SaaS applications, you're at the cutting edge of your industry. But have you addressed the compliance [...]
Spanning Backup for Office 365: Restoring from Litigation Hold
This video shows you all of the steps involved in restoring email from litigation hold back into a user's Exchange Online account, and how that method [...]
Millar, Inc. User Story: Spanning Backup for Office 365
Data protection and HIPAA compliance is critical for companies in the healthcare domain, like Millar, Inc. They use Spanning Backup for Office 365 to [...]
The Definitive Guide to Backup for Salesforce
Looking for the right solution to protect your critical Salesforce data? Use this guide to learn the truth about SaaS data loss and how to identify a [...]
10 Reasons You Need SaaS Data Protection for Office 365
Your mission: find out why SaaS data protection is critical to success with Office 365. See the infographic to complete this mission and learn how to [...]
Spanning Backup for Microsoft 365: Product Datasheet
Spanning Backup provides daily, automated backup and accurate restore, ensuring that your Office 365 data is protected, available, and recoverable, no [...]
AMAG Pharmaceuticals User Story: Spanning Backup for Google Workspace
Steve Simmons, Director of IA for AMAG Pharmaceuticals shares how Spanning Backup for Google Workspace ensured business continuity with effortless bac [...]
ESG Lab Test Drive: Spanning Backup for Google Workspace
ESG's IT spending trends report for 2014 shows that the adoption of cloud applications continues to become more mainstream, moving traditional workloa [...]
The Definitive Guide to Backup For Google Workspace
You’ve found the perfect cloud-based productivity suite in Google Workspace for Work. Now you just need to find a way to keep your data safe from lo [...]
Alzheimer’s Association® User Story: Spanning Backup for Google Workspace
Read how the Alzheimer's Association that has taken great strides towards a "world without Alzheimer's" trusts Spanning Backup as the safety net for t [...]
Volusion User Story: Spanning Backup for Salesforce
Volusion’s robust and stunning all-in-one e-commerce solutions are used by 180,000+ businesses. Read how Spanning Backup for Salesforce keeps all th [...]
9 Ways to Make Your Auditors Love You
No one loves the word audit; in fact, you'd be hard-pressed to find anyone who even likes it. But whether you like it or not, auditors are coming to m [...]
Muscat Overseas Group | Spanning Backup for Google Workspace
Muscat Overseas Group is a 40-year-old conglomerate representing renowned and diverse businesses such as JCB, Volvo Penta, Syngenta, Technip, Bloomber [...]
3 Ways to Restore Salesforce Data
How do you know when you need to do more to protect your Salesforce data? Learn about the best methods for restoring your lost Salesforce data and mor [...]
Developer Guide: How to Make Your Force.com Canvas App Available on Salesforce1
With the launch of Salesforce1, it's becoming increasingly important to have your Force.com applications available on mobile. [...]
SendGrid User Story: Spanning Backup for Google Workspace & Salesforce
Find out why SendGrid goes beyond the weekly manual export for Salesforce to keep critical data fully protected from loss. [...]
UMD Smith School of Business Customer Interview: Spanning Backup for Google Workspace
See why the Robert H. Smith School of business chose Spanning Backup over the competition to keep this top-ranked institution's data safe and accessib [...]
IDG Quick Pulse Survey Report: Cloud Data at Risk
Experts agree that relying on SaaS vendors to back up and restore your data is dangerous. Yet that's exactly what huge portions of the business world [...]
Clifton College User Story: Spanning Backup for Google Workspace
Read why this Historic Institute trusts Spanning with protecting confidential student data. [...]
IDG Quick Pulse Survey Report: Cloud Data at Risk
Experts agree that relying on SaaS vendors to back up and restore your data is dangerous. Yet that's exactly what huge portions of the business world [...]
Chattanooga Zoo User Story: Spanning Backup for Google Workspace
Learn why Blake Curtis knew Spanning Backup was the best solution for his organization just days into their free 14-day trial. [...]
Pivotal | Spanning Backup for Google Workspace
Pivotal's cutting edge technology depends on secure and powerful solutions to support their rapidly expanding business. See how Spanning Backup keeps [...]
St. Stephen’s Episcopal School User Story: Spanning Backup for Google Workspace
Read why one of Austin, Texas' most historic schools chose Spanning to keep their Google Workspace for Education data safe from loss and always access [...]
Solution Overview: Spanning Backup for Google Workspace for Education
Google Workspace may be revolutionizing education, but it isn't immune from data loss due to hackers, malicious insiders, human error, sync malfunctio [...]
The Animal Foundation User Story: Spanning Backup for Google Workspace
The Animal Foundation must focus on saving and improving lives each day, not data loss. See how Spanning helps keep them focused on this mission by gi [...]
Spanning Backup for Salesforce: Product Datasheet
Learn about the features, benefits and capabilities of Spanning Backup for Salesforce. [...]
Hamline University | Spanning Backup for Google Workspace
Hamline University found not only a solid backup and recovery solution in Spanning, but also a trusted partner they can count on no matter what the fu [...]
Improved Status Updates: Spanning Backup for Google Workspace
See the new and improved status reporting in Spanning Backup for Google Workspace and rest easy knowing your backups are completely transparent. [...]
Attack! Marketing User Story: Spanning Backup for Google Workspace
Discover why Attack! Marketing trusts Spanning with their Google Workspace data, and why they may be adopting our backup for Salesforce.com, too! [...]
Prevent Data Loss & Ensure Compliance for SaaS Apps — On-Demand Webinar
As the number of compliance and regulatory mandates that require you to maintain and demonstrate controls over critical data continues to grow, so doe [...]
Are Your Google Drive Files Corrupt?
If you use the web and desktop versions of Google Drive, you should check regularly to make sure sync errors haven't corrupted your files. We show you [...]
Transfer Ownership of a Google Calendar Event: Spanning Backup for Google Workspace
If an employee's Google account gets deleted, they might take a shared meeting with them. Here's how to get that meeting back with you as the owner. [...]
Wolfgang Career Coaching User Story: Spanning Backup for Google Workspace
Take a look at the many reasons the CEO of this successful small business chose Spanning to achieve peace of mind about her Google Workspace backup. [...]
Second Baptist School User Story: Spanning Backup for Google Workspace
Find out how Second Baptist stopped losing data and started breathing easier with Google Workspace backup from Spanning. [...]
Smith School of Business, University of Maryland | Spanning Backup for Google Workspace
Find out how Spanning Backup handles Google Workspace backup for the Smith School of Business. [...]
9 Essentials for a Complete Cloud-to-Cloud Backup Solution
In this white paper, we discuss the must-haves for a proper cloud-to-cloud backup and recovery solution. [...]
Mannheim School District 83 User Story: Spanning Backup for Google Workspace
See how Spanning Backup quietly handles Google Workspace backup for Mannheim School District 83. [...]
mbox File Export — Email Backup: Spanning Backup for Google Workspace
In Spanning Backup, there’s an option to export your email files to an mbox format, but many people wonder, “What do I do with the exported file?� [...]
Trust and Transparency Matter Most to Kendra Scott When it Comes to Google Workspace Backup
Nathan Toups, IT lead for fashion jewelry retailer Kendra Scott, discusses why Spanning Backup is so important to this rapidly growing company. [...]
How Redfin Keeps Cloud-Based Data Safe
Read this article featured in CIO Magazine to learn how Redfin is backing up critical documents stored in Google Drive with Spanning Backup. [...]
BlackLocus Innovation Lab User Story: Spanning Backup for Google Workspace
See how Spanning Backup is freeing this fellow startup company from worry about data loss. [...]
Tquila Relies on SaaS App Backup for Born-in-the-Cloud Business Model
Learn from Tquila's Bashir Qaasim why backup and restore for Google Workspace and Salesforce are key to keeping business moving in the cloud. [...]
9 Gauge Partners LLC User Story: Spanning Backup for Google Workspace
Find out how 9 Gauge was saved from a sync error by Google Workspace backup from Spanning. [...]
MBA Agency
See how MBA Agency’s 6,000 Google Contacts were restored with Spanning Backup for Google Workspace.. [...]