5 Things Every MSP Should Know About HIPAA
If your clients include healthcare providers or payers, understanding how to comply with HIPAA isn’t just important – it is an absolute requirement for MSPs.
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) applies not just to healthcare providers, like doctors and dentists, and to payers, like health plans; it also applies to vendors and suppliers who require access to protected health information (PHI and ePHI) to perform their work. Those vendors and suppliers are referred to in HIPAA regulations as Business Associates (BAs), and as an MSP, if you have healthcare clients, you likely share in your clients’ risks.
There is no official “certification” in HIPAA recognized by the Federal government, therefore MSPs who work with healthcare providers or payers need to educate themselves on HIPAA compliance.
 Here are the top 5 things MSPs should know about HIPAA.
Here are the top 5 things MSPs should know about HIPAA.
1. HIPAA penalties could put an MSP out of business.
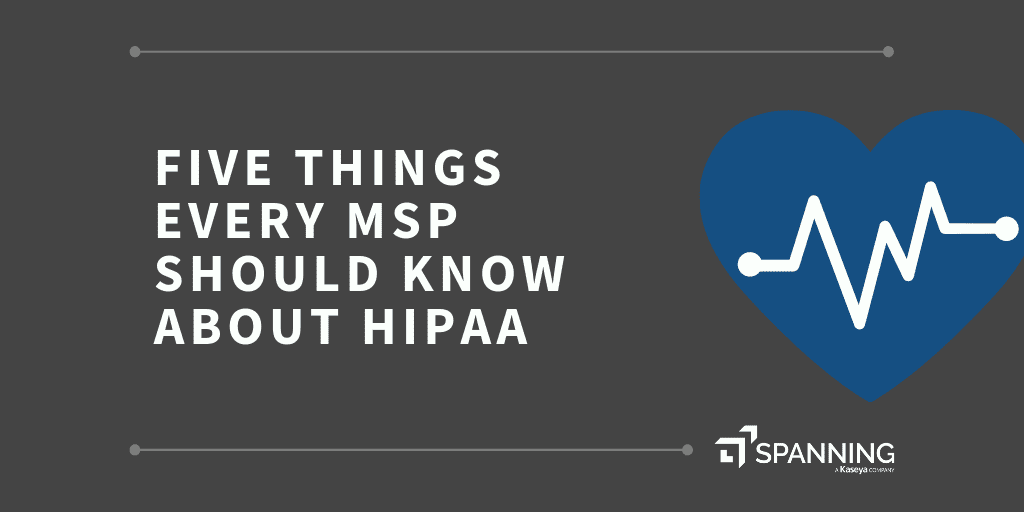
Huge healthcare provider and payer organizations make HIPAA compliance part of their IT planning, and have the staffing and budgets to do so. Smaller organizations don’t always devote resources to HIPAA compliance, but they should. If you’re an MSP working with small healthcare providers or plans, penalties for non-compliance could easily put your company out of business.
From January through September 2018 alone, there were 55 cases resulting in penalties of nearly $79M USD. There’s more – cases not filed but upheld in 2018 include:
- MD Anderson paying $4.3M penalty for HIPAA encryption violations. The University of Texas MD Anderson Cancer Center in Houston must pay $4,348,000 in civil penalties for HIPAA violations related to the organization’s encryption policies.
- Fresenius Medical Care North America paying $3.5 million for data breaches. The Fresenius network comprises dialysis care, outpatient cardiac and vascular labs, urgent care centers, and post-acute providers.
- Filefax, a now-closed medical records management company, paying a $100K fine on its shuttered facility for 2015 HIPAA violation. A receiver appointed to liquidate the assets of Filefax, a now-closed medical records management company, will pay $100,000 out of the receivership estate. Filefax had disclosed the confidential information of 2,150 patients in medical records left at a shredding and recycling facility.
Need more convincing that HIPAA presents financial risk for non-compliance? See the HSS site for an extensive list of violations.
2. Security assessments are an MSP’s friend.
HIPAA provides MSPs a new way to build their relationships with clients as a trusted adviser. MSPs should conduct organization-wide initial HIPAA Risk Assessments for their healthcare clients. They can use the HSS’s Security Risk Assessment Tool, or similar tools in the Kaseya portfolio, to guide them through the process and collect the necessary data and information.
A deep-dive HIPAA assessment will define what needs to be changed immediately, what new technologies should be put in place, and how MSP services such as RMM, cloud-to-cloud backup, and authentication and access management can help an MSP’s clients achieve HIPAA compliance.
HIPAA requires all PHI data that is transmitted electronically (ePHI) to be protected, which is best done by strong encryption. In fact, if the data is properly encrypted, the MSP and their client may be immune from penalty if that data is breached or a device is lost. (Note: if an MSP’s client uses cloud-based platforms like Microsoft Office 365, this still applies. As discussed here, cloud suite providers are secure, but they cannot protect your clients’ data from their errors, programmatic errors, or from malicious acts.)
Once the initial risk assessment is completed and clients understand their actual risk exposure, the MSP can deploy Audit Guru for HIPAA from RapidFire to provide compliance-as-a-service with recurring revenue.
3. MSPs are responsible when their clients run afoul of HIPAA.
An MSP’s healthcare payer and provider clients are referred to as Covered Entities; by definition, they are responsible for being in compliance with all aspects of HIPAA. MSPs who work with healthcare clients are referred to as Business Associates (BA) and are equally responsible for their clients’ data security. For more details on what a Business Associate’s responsibilities are and sample BA Agreement, see the HHS site here.
Very large hospitals and other big healthcare organizations include HIPAA compliance in their IT planning. They budget to pay for the technology that supports compliance, and train their staff in ePHI and HIPAA best practices. While large organizations have prioritized reducing the risks from non-compliance, HHS is clear that HIPAA compliance applies to even small organizations. “All HIPAA covered entities and business associates are required to conduct an accurate and thorough assessment of the potential risks and vulnerabilities to the confidentiality, integrity, and availability of electronic protected health information held by their organization.”
As a trusted IT advisor and a HIPAA Business Associate, an MSP must ensure all their healthcare provider and payer clients are in compliance. MSPs should advise their small healthcare clients that a HIPAA fine could be financially devastating and put them out of business — HIPAA is not just a concern for large organizations.
4. In your role as a trusted adviser, your clients need to understand that documentation and robust encryption are not optional.
HIPAA rules require that MSPs, as HIPAA Business Associates, must document the protective measures in place for ePHI (electronic Personal Health Information). Within Kaseya’s IT Complete portfolio, RapidFire Tool’s Network Detective HIPAA Assessment module and Audit Guru for HIPAA Compliance Solution automatically generate all the compliance documentation required by HIPAA.
Encryption is one area where HIPAA isn’t completely explicit. Instead, the HHS talks about doing “what is reasonable and appropriate” to protect ePHI, and then notes:
“In meeting standards that contain addressable implementation specifications, a covered entity will do one of the following for each addressable specification:
- Implement the addressable implementation specifications
- Implement one or more alternative security measures to accomplish the same purpose
- Not implement either an addressable implementation specification or an alternative”
This basically says the healthcare organization or their BA must find an effective way to secure data — and for ePHI compliance, this means that data in transit or at rest must be secured. While HIPAA doesn’t specifically require encryption, encryption is the only reasonable and viable way to meet HIPAA demands that ePHI be always protected.
As your healthcare clients’ trusted IT adviser, part of your responsibility to your clients is to ensure they’re HIPAA compliant, even if HHS guidance is not proscriptive.
5. The best defense in case of an audit is “Evidence of Compliance.”
Evidence of Compliance is when a healthcare organization produces documentation that shows its efforts to adhere to HIPAA regulations. The documents should be able to prove the steps that were taken to identify and mitigate security risks related to HIPAA. As a trusted advisor, MSPs can support their clients in voluntarily conducting internal audits on a regular basis in order to be able to produce the Evidence of Compliance. In the event of an external government audit, if the healthcare organization cannot produce Evidence of Compliance it can be slapped with large fines for “benign neglect”… even if there is no breach.
Another HIPAA need-to-have is a security incident response plan (SIRP.) A SIRP will document what will be done in the case of security breach or other security event, will monitor to show whether or not attacks have taken place, and will support Evidence of Compliance efforts. While no one approach is recommended by HHS — “In order to maintain a flexible, scalable and technology neutral approach to the Security Rule, no single method is identified for addressing security incidents that will apply to all covered entities” — MSPs should help their clients be prepared to document security events, whether attempted or an actual breach. For more details on what HHS requires, see their site here. An MSP deploying Kaseya IT Complete portfolio solutions like Audit Guru for HIPAA is best equipped for an audit because the Evidence of Compliance is automatically generated and kept up to date.
All MSPs with healthcare payer or provider clients should meet with those clients to review their current HIPAA compliance plans. Grow your business by being your clients’ trusted adviser — learn more about HIPAA compliance here.